Crooks use software skimmer that pretends to be a security firm
Security Affairs
NOVEMBER 16, 2020
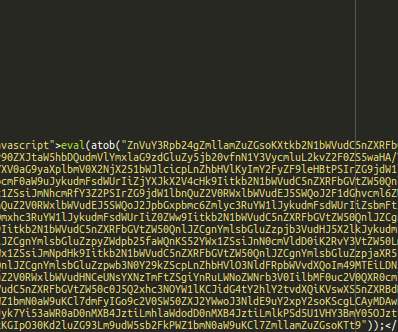
Upon execution, the code gathers any data from form fields, such as credit card and billing details, and exfiltrates it to a remote gateway using a GET request with plaintext parameters. “The payment data exfiltration takes place via an <img> tag whose src parameter is changed to hxxps://terminal4.veeblehosting[.]com/~sucurrin/i/gate.php









Let's personalize your content