Russia-linked APT28 compromised Ubiquiti EdgeRouters to facilitate cyber operations
Security Affairs
FEBRUARY 28, 2024
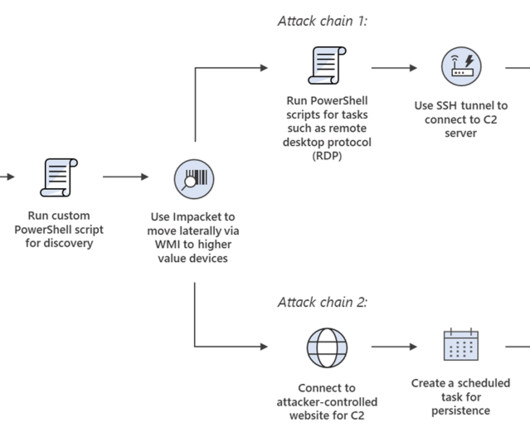
The Federal Bureau of Investigation (FBI), National Security Agency (NSA), US Cyber Command, and international partners released a joint Cybersecurity Advisory (CSA) to warn that Russia-linked threat actors are using compromised Ubiquiti EdgeRouters (EdgeRouters) to evade detection in cyber operations worldwide. ” concludes the report.













Let's personalize your content