LockFile Ransomware uses a new intermittent encryption technique
Security Affairs
AUGUST 31, 2021
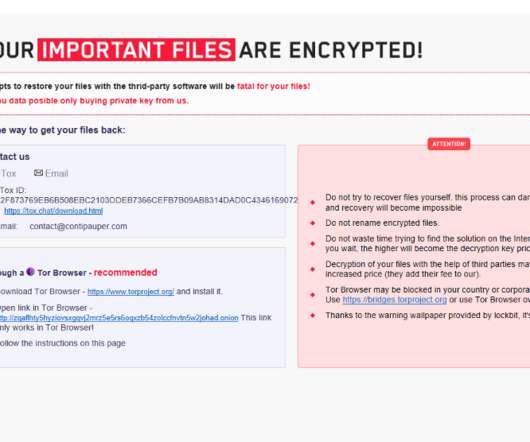
The popular security expert Kevin Beaumont was one of the first researchers to report that the LockFile operators are using the Microsoft Exchange ProxyShell and the Windows PetitPotam vulnerabilities to take over Windows domains. The HTA ransom note used by LockFile closely resembles the one used by LockBit 2.0 Pierluigi Paganini.








Let's personalize your content