New Linux Malware Shikitega Can Take Full Control of Devices
eSecurity Planet
SEPTEMBER 15, 2022
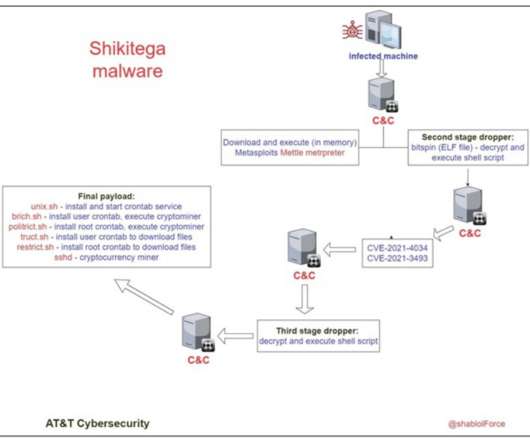
The infamous XMRig mines Monero cryptocurrency that is known to be anonymity-focused, as it’s particularly hard to trace back. AT&T labs provided a list of IoCs (indicators of compromise) that system administrators can use to add specific rules to security solutions. Cybercriminals Use C2 Servers to Deploy Cryptominer.









Let's personalize your content