Service providers that operate 5G networks face many challenges related to their highly distributed infrastructure. While Kubernetes presents a promising solution for addressing these challenges, service providers and Mobile Network Operators (MNOs) need to mitigate the data security challenges that arise from using Kubernetes for 5G deployments. Thales CipherTrust Transparent Encryption application was developed to help users secure data in persistent volumes attached to pods running on Red Hat OpenShift, a unified platform to build, modernize, and deploy applications at scale. Thales CipherTrust Transparent Encryption application and Kubernetes operator are both certified on the Red Hat OpenShift Container Platform and available in the Red Hat Ecosystem Catalogue.
Kubernetes is an open source container orchestration software solution that can help service providers with 5G Cloud-native Network Functions (CNFs), since containers are essential to getting cloud software and services to operate at scale. With an application platform such as Red Hat OpenShift, cloud-native microservice applications can span hosts across on-premise, public, private, or hybrid clouds. For this reason, Red Hat OpenShift is an ideal platform to build, deploy and runcloud-native applications that require rapid scaling, like real-time data communications.
MNOs’ challenges in the highly distributed 5G environment range from managing their complex IT infrastructure yet also ensuring software applications run efficiently across all layers. This same infrastructure also needs to be flexible, in order to meet ever evolving business and performance needs.
For these reasons, 5G networks require dynamic and scalable infrastructures built on a services-based architecture. Operations can be deployed across several geographically distributed environments, often creating a significant challenge for service providers. Red Hat OpenShift is the leading Kubernetes-based application platform, enabling a proven solution for service providers by allowing efficient management of containers within the 5G network infrastructure.
The challenges for securing Kubernetes in 5G environments
The rise of 5G technology has resulted in a massive surge in the volume of generated data. This data is stored across numerous systems and platforms, including Kubernetes. Securing data at rest within Kubernetes is of the utmost importance, as unauthorized access or breaches could have severe implications. Using Kubernetes out of the box presents several challenges for security admins.
- Kubernetes security configuration: When deploying Kubernetes, the security controls are not pre-configured. It is the operator’s responsibility to understand how these controls work and ensure they are securely configured. This can be challenging, and it's important to be aware of the potential for misconfigurations.
- Securing workloads deployment: Securing workloads in Kubernetes can be challenging for developers and application teams who may not be well-versed with the platform, whether using a pre-configured security-enabled Kubernetes distribution or building their own cluster and security measures.
- Built-in security vulnerabilities: Although Kubernetes provides access controls and security features to build security-focused clusters, the initial setup may leave security vulnerabilities. To provide Kubernetes clusters and containers with enhanced security features, organizations should make appropriate modifications to workload, cluster, networking, and infrastructure configurations.
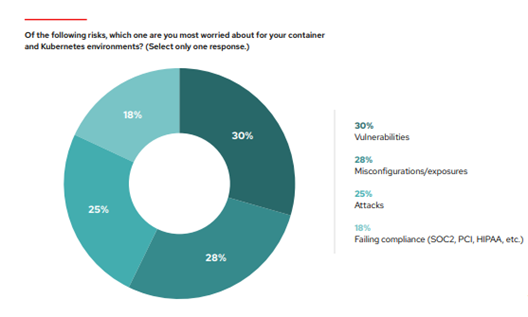
Source: https://www.redhat.com/en/resources/state-kubernetes-security-report-2023
Kubernetes faces significant challenges in terms of security due to its intricate nature and susceptibility to vulnerabilities and misconfigurations. Inadequate monitoring can impede the identification of these issues, particularly when deploying multiple containers, making it arduous to detect potential risks. Consequently, this creates an opportunity for malicious hackers to exploit weaknesses and gain unauthorized access to your system.
To mitigate such security challenges, several measures can be taken:
1. Enhance security using protective modules like AppArmor and SELinux.
2. Enable role-based access control (RBAC) to enforce mandatory authentication for every user and regulate their access privileges based on their assigned roles.
3. Implement the segregation of containers to separate front-end and back-end functionalities, ensuring maximum security by concealing the private key through regulated interaction.
4. Employ data encryption techniques with pre-shared keys to safeguard all data stored within the containers and databases, leveraging RBAC for robust protection.
By implementing these security measures, you can fortify your Kubernetes environment and minimize the risk of unauthorized breaches and data compromise.
Implementing robust measures to secure data at rest is imperative to mitigate risks and safeguard the confidentiality, integrity, and availability of critical information. These controls must include data-at-rest encryption, strong access controls to prevent unauthorized access to data, hardening container images, and consistent auditing to detect any suspicious attempts to access containers and data.
Data security in Kubernetes also involves protecting data that is stored on persistent volumes, which are used to provide data storage for stateful applications. As modern apps are increasingly built using containers and microservices, Kubernetes delivers, deploys, and manages these applications faster and more efficiently. However, several risks are threatening the security of data and apps within Kubernetes:
- Privileged user abuse.
By default, containerized processes operate with root privileges, granting administrators complete access to all tenant secrets. This degree of unrestricted access presents numerous risks. Organizations may be vulnerable to privilege escalation attacks if the administrators' accounts are compromised or stolen.
- Cross container access.
Improperly configured access controls can lead to the unauthorized exposure of private information to multiple containers. Additionally, when containers are hosted in shared virtualized or cloud environments, confidential data may be compromised and accessible to unauthorized third parties.
- Compliance risks.
Compliance regulations often demand strict access management and thorough auditing of data access. Unfortunately, security teams may face challenges in effectively controlling and monitoring access to data contained within images and containers. This can make it challenging for them to adhere to necessary security protocols and cryptography algorithms and comply with regulatory requirements.
Thales Solution for Kubernetes Data Security
With Thales CipherTrust Transparent Encryption for Kubernetes, you can safeguard confidential data on persistent volumes linked to pods operating on Red Hat OpenShift via encryption, process and user-based access control, and data access logging. This powerful solution, certified on Red Hat OpenShift, empowers developers to impose security measures within Red Hat OpenShift containers. CipherTrust Transparent Encryption can apply data security to individual containers and external storage accessible from them using the Container Storage Interface.
Service providers operating 5G networks can enjoy multiple benefits from investing inThales CipherTrust Transparent Encryption for Kubernetes certified on Red Hat OpenShift.
Comprehensive data security safeguards
With CipherTrust Transparent Encryption for Kubernetes, security teams can now ensure data security controls within containers using the Container Storage Interface (CSI). Service providers can apply access control, encryption, and data access auditing on a per-container basis. Persistent volumes attached to containerized applications are encrypted, and data access can be restricted to authorized users and processes.
Transparent encryption
Transparent encryption enables service providers to ensure data security measures without altering their applications, containers, or infrastructure configurations. The solution accommodates popular microservices deployment models, allowing for consistent protection policies across all persistent volumes linked to an application pod or customized encryption and access control for each persistent volume within a Kubernetes cluster.
Granular access controls and visibility
With CipherTrust Transparent Encryption for Kubernetes, service providers and MNOs have the necessary visibility and control to meet even the most rigorous regulations, policies, and mandates. They can create detailed access policies based on particular users, processes, and resources within containers. Additionally, the solution provides container isolation, ensuring that only authorized containers can access sensitive information.
To learn more about how Red Hat uses Thales CipherTrust Transparent Encryption to Protect Containers, check out this Solution Brief. You can also watch this demonstration to see CipherTrust Transparent Encryption for Kubernetes in action.

 Chen Arbel | Associate Vice President, Business Development, 5G
Chen Arbel | Associate Vice President, Business Development, 5G