The cloud has enabled organizations to create data stores across the globe at breakneck speeds. Organizations can now leverage the cloud to reach a broader user base, accelerate application time to value, and deliver new ways of connecting with employees, customers, and partners. However, with all that the cloud offers, it has ushered in the need for more robust security controls, especially when storing sensitive and critical data. One tried and true way of protecting sensitive and critical data is through encryption. However, as data stores scale, so do the number of cryptographic keys that must be managed. The traditional approach of managing keys in different silos delivers diminishing returns in terms of manhours and policy control for different key types. Centralized key management was introduced to resolve this key management challenge, breaking down the silos and significantly reducing the time needed to manage keys while delivering consistent policies wherever data is kept.
You Cannot Manage What You Cannot Find
One of the major obstacles organizations face when considering a centralized key management approach is taking inventory of their keys and implementing them within the key management solution. To implement a key management solution, you must first understand where your cloud-based keys reside and how many you have. Across large organizations, it is difficult to gain complete visibility into Azure Key Vaults and Google Key Rings created by all departments. Even if you can locate all your keys within your cloud instances, contending with hundreds of projects and thousands of keys makes it unmanageable to manually add all the needed key management services. An effective key management strategy requires a better way to detect the key management service containers, whether they are Azure Key Vaults or Google Key Rings, and incorporate them within your overall key management strategy. This poses a couple of questions:
1. How can you confidently identify all your key management services and their keys within your cloud environment without much human intervention?
2. How can you know when new key management services and their keys are introduced into your environment and add them automatically or after review?
Automating the Discovery of Keys in Your Cloud Instances
Thales CipherTrust Cloud Key Management (CCKM) has implemented an easy-to-use tool to help users automatically discover keys in their Azure Key Vaults and Google Key Rings and quickly add them to their CCKM deployments. This capability is available in CCKM version 2.15 and beyond. To perform this function is a simple process as illustrated below:

The simple key discovery process is defined within the CCKM interface.
The graphic shows the process of discovering your cloud-based key management service. First, you establish a connection to the cloud(s). Second, you define the key management service discovery criteria. Then, you run the key management service discovery process on a recurring schedule or on an ad hoc basis. Once these simple steps are completed, you will be presented with any new key management service within your Google or Azure environment that was not previously defined in your CCKM.
Continually Discover New Keys
As new keys are added due to scaling the cloud environment or adding new data stores, the CCKM, using the recurring scheduled key discovery process, will identify these new key management services and keys within. The scheduling process within the CCKM allows you to perform a recurring search for new key management services at a defined time, for example, daily at midnight. Once the key management services are added CCKM can leverage its’ Refresh function to synchronize keys from selected cloud accounts. This process ensures that new keys introduced within your cloud environments and stored within Google Key Ring or Azure vaults will be discovered.
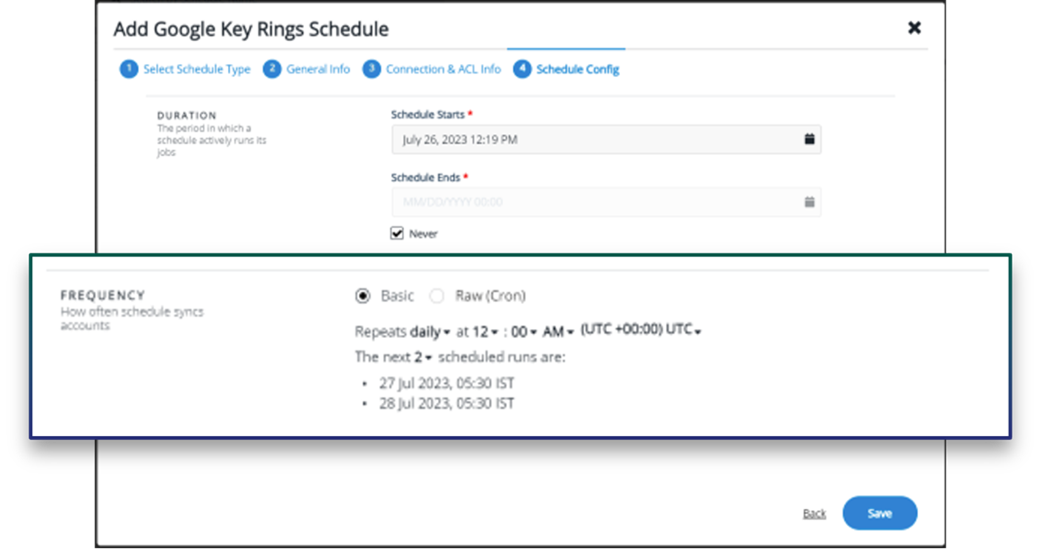
Establish a recurring schedule to discover new keys within the environment.
Review and Automatically Add New Keys
Once you discover your key management services the next logical step is to incorporate them within the existing management operations and apply existing policies to them. Some organizations may have the discovered key management services automatically added to the existing system and processes, whereas others may want to review the key management services before incorporating them. CCMK allows you to choose how you wish to handle newly discovered key management services.

CCKM allows you to define if a job should only discover or discover and add new key management services.
Wrap Up
As organizations continue to adopt and secure cloud-based data storage, effectively managing cryptographic keys is critical. Moving to a centralized key management approach requires identifying the key management services within your cloud environments and systematically identifying new ones as they are introduced. Thales CipherTrust Cloud Key Management allows organizations to automatically detect the key management services in their cloud environment and integrate them into their overall cloud key management strategy. It also delivers greater operational efficiency and ensures consistent policy across all key types.
See more at our Cloud Key Management Demo: Automatically Detect Cloud Key Services.
To learn more, visit our CipherTrust Cloud Key Management page.

 Brian Robertson | Principal Product Marketing Manager
Brian Robertson | Principal Product Marketing Manager