Exploited TP-Link Vulnerability Spawns Botnet Threats
Data Breach Today
APRIL 17, 2024
Chinese router manufacture TP-Link in June patched a command injection vulnerability.

 vulnerabilities-threats
vulnerabilities-threats 
Data Breach Today
APRIL 17, 2024
Chinese router manufacture TP-Link in June patched a command injection vulnerability.

Data Breach Today
APRIL 19, 2024
Threat Actor Exploited Ivanti Zero-Day Vulnerabilities in Cyberattack A nation-state threat actor gained access into an unclassified research and development network operated by MITRE, a non-profit that oversees key federal funded research and development centers for the U.S. government, the organization confirmed on Friday.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Jamf
FEBRUARY 17, 2023
Jamf Threat Labs investigated a WebKit vulnerability that was exploited in the wild. This blog explores what the vulnerability looked like in the code and the patches Apple applied. Attackers can exploit CVE-2022-42856 to control code execution within WebKit, giving them the ability to read/write files.

Data Breach Today
APRIL 15, 2024
Company Released a Hotfix to the Command Injection Vulnerability Firewall appliance manufacturer Palo Alto Networks rushed out a hotfix Friday to a command injection vulnerability present in its custom operating system after security researchers spotted a campaign to exploit the zero-day starting in March, likely from a state-backed threat actor.

Speaker: Naresh Soni, CTO, Tsunami XR
The pandemic has led to new data vulnerabilities, and therefore new cyber security threats. By understanding the latest threats and their solutions, you can come out of this crisis stronger than ever--without breaking the bank. He will cover: Types of vulnerabilities that need to be your focus today.

Data Breach Today
MARCH 22, 2024
UNC5174 Exploited F5 BIG-IP and ScreenConnect Vulnerabilities A likely Chinese hacker-for-hire used high-profile vulnerabilities in a campaign targeting a slew of Southeast Asian and U.S. governmental and research organizations, says threat intel firm Mandiant.
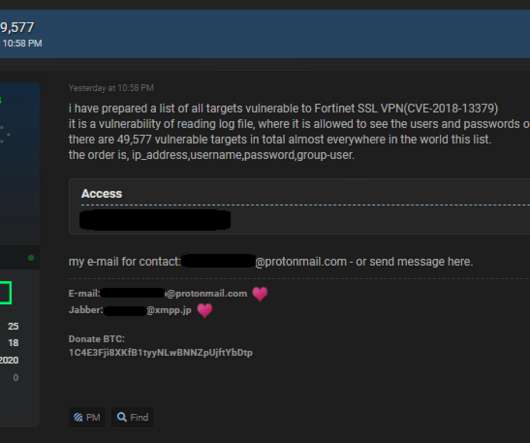
Security Affairs
NOVEMBER 22, 2020
A threat actor has published online a list of one-line exploits to steal VPN credentials from over 49,000 vulnerable Fortinet VPNs. A threat actor, who goes online with the moniker “pumpedkicks,” has leaked online a list of exploits that could be exploited to steal VPN credentials from almost 50,000 Fortinet VPN devices.

Advertisement
With cyber threats increasing, and businesses becoming more vulnerable, the need to invest in the right cybersecurity solutions has never been more important. How ThreatLocker can help you mitigate cyber threats with our unique endpoint solutions. And more!

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022.
Let's personalize your content