Data Privacy: Why It Matters To The Rest Of Us
Thales Cloud Protection & Licensing
JANUARY 21, 2024
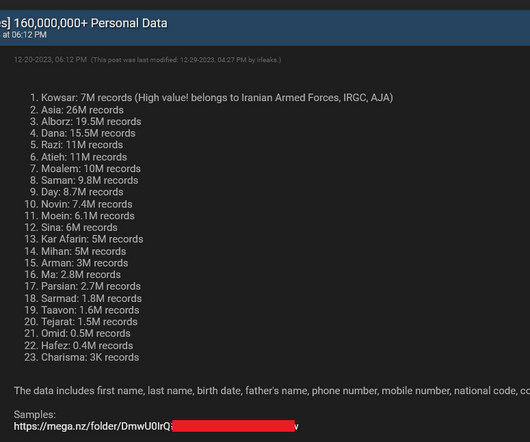
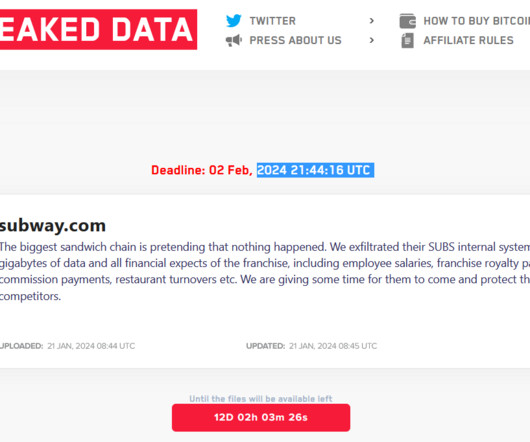
Data Privacy: Why It Matters To The Rest Of Us madhav Mon, 01/22/2024 - 04:47 It seems that there are no limits to the number of data breaches. Company size is not a determinant of victimization, nor is industry or sector. All are equally viable targets. Some of the events are newsworthy, while others stay below the public’s awareness or attention. Most companies must grapple with difficult questions of how to recover from a breach; however, when the typical person hears about a data breach, the







































Let's personalize your content