STEPS FORWARD Q&A: Will ‘proactive security’ engender a shift to risk-based network protection?
The Last Watchdog
OCTOBER 4, 2023
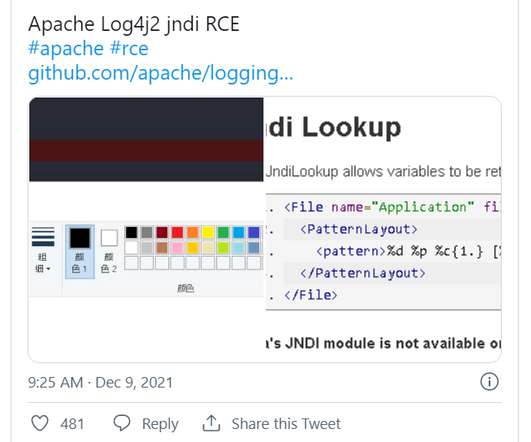
Companies are obsessed with leveraging cloud-hosted IT infrastructure and the speedy software development and deployment that goes along with that. Notably, some 79 percent of enterprises recently polled by Omdia consider this risk-ranking capability indispensable. Is that fair?















































Let's personalize your content