ISMG Editors: Day 2 Overview at RSA Conference 2023
Data Breach Today
APRIL 25, 2023
ISMG editors at the RSA Conference 2023 in San Francisco discuss the hot topics this year, from the looming risk of the metaverse and our reality to the latest approach to cloud development.







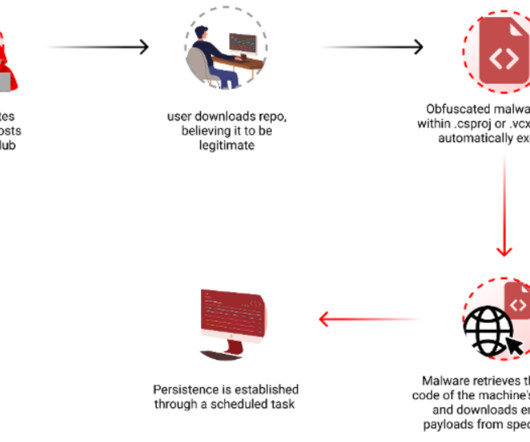









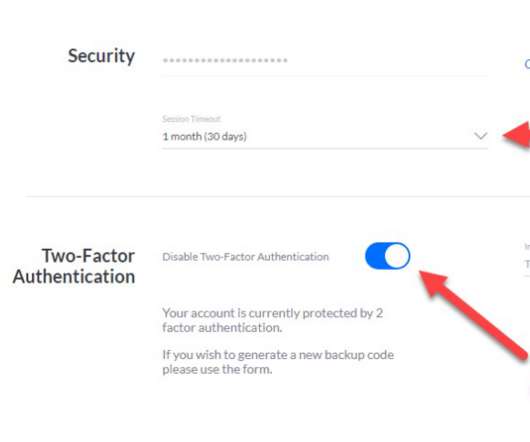

































Let's personalize your content