American fast-fashion firm Hot Topic hit by credential stuffing attacks
Security Affairs
MARCH 29, 2024
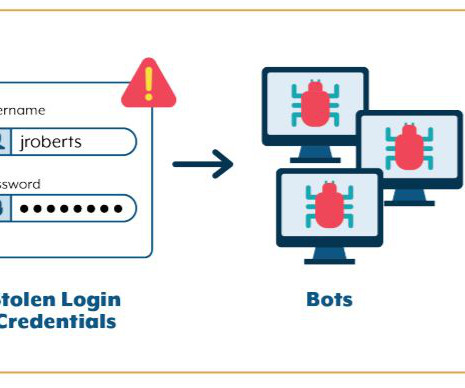
Hot Topic suffered credential stuffing attacks that exposed customers’ personal information and partial payment data. Hot Topic, Inc. is an American fast-fashion company specializing in counterculture-related clothing and accessories, as well as licensed music. The company also recommends changing the account password.

















































Let's personalize your content