Researcher Strips ROM For Binary Code
Data Breach Today
APRIL 25, 2024
Improved Tooling Makes Such Attacks More Likely Research shows that attackers can physically extract secrets embedded into read-only memory on a shoestring budget. The equipment involves a polishing wheel, a jig and an optical microscope. The attack sounds impossible "until it’s observed for real," said Tony Moor, a IOActive researcher.














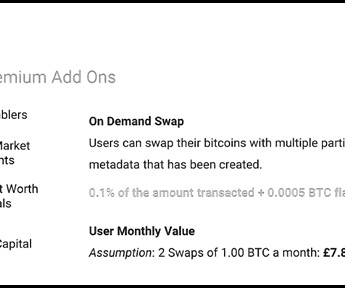























Let's personalize your content