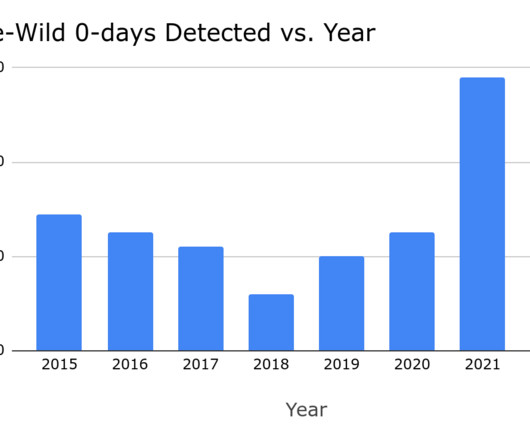
In 2022, more than 40% of zero-day exploits used in the wild were variations of previous issues
Security Affairs
JULY 30, 2023
The popular Threat Analysis Group (TAG) Maddie Stone wrote Google’s fourth annual year-in-review of zero-day flaws exploited in-the-wild [ 2021 , 2020 , 2019 ], it is built off of the mid-year 2022 review. Google's 2022 Year in Review of in-the-wild 0-days is out!













































Let's personalize your content