Commercial spyware vendors are behind most zero-day exploits discovered by Google TAG
Security Affairs
FEBRUARY 6, 2024
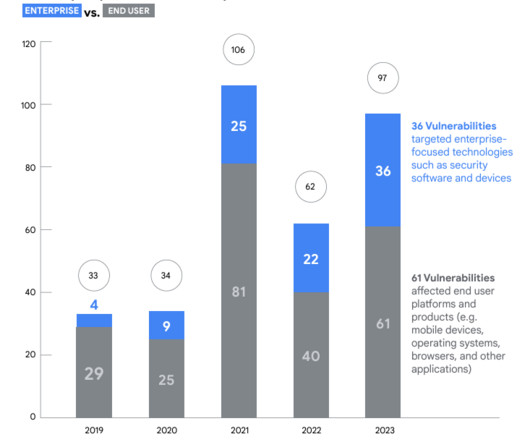
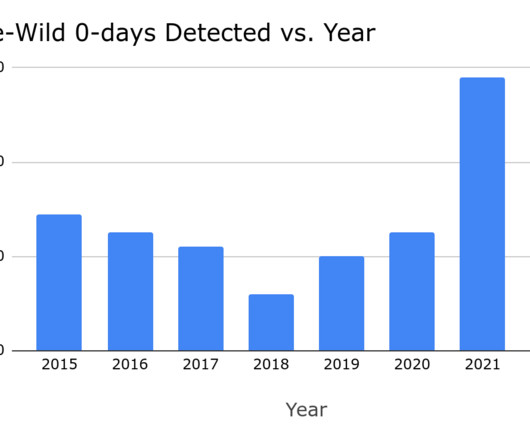
Google’s TAG revealed that Commercial spyware vendors (CSV) were behind most of the zero-day vulnerabilities discovered in 2023. Google’s TAG tracked the activity of around 40 CSVs focusing on the types of software they develop. ” reads the report published by Google. ” concludes Google.










































Let's personalize your content