AV-Comparatives Reveals Results of Long-Term Tests of 19 Leading Endpoint Security Solutions
Dark Reading
DECEMBER 28, 2021
The Business Security Test is a comprehensive investigation of corporate endpoint security solutions on the market.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 solutions endpoint-security
solutions endpoint-security 
Dark Reading
DECEMBER 28, 2021
The Business Security Test is a comprehensive investigation of corporate endpoint security solutions on the market.

OpenText Information Management
JULY 6, 2021
The thought that a chain is only as strong as its weakest link is something that can keep IT security professionals awake at night. Today, many large organizations are managing more than 50,000 individual endpoints, with some responsible for in excess of 500,000.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
JANUARY 3, 2024
SentinelOne to Add CNAP Capabilities for 'Best of Breed' Security Platform Endpoint security firm SentinelOne is set to acquire PingSafe for an undisclosed sum of cash and stock.

Security Affairs
FEBRUARY 18, 2024
Cybersecurity firm ESET has addressed a high-severity elevation of privilege vulnerability in its Windows security solution. Below is the list of impacted programs and versions: ESET NOD32 Antivirus, Internet Security, Smart Security Premium, Security Ultimate 16.2.15.0 10.0.10017.0, 10.0.10017.0, 10.0.10017.0,

Advertisement
With cyber threats increasing, and businesses becoming more vulnerable, the need to invest in the right cybersecurity solutions has never been more important. However, all too often finding the right solutions can be a daunting task, especially if you’re not sure what you’re looking for. And more!

The Last Watchdog
JULY 1, 2022
This raises the concerns of corporate data security in remote working that still stand as a key challenge that organizations are trying to navigate, workforce productivity being the second. Managing endpoints securely . This is also why looking for a solution with a holistic approach can be such a tipping point.

eSecurity Planet
JANUARY 11, 2024
Ransomware remains just one of many different threats and as security teams eliminate key vectors of attack, adversaries will shift tactics. Unmanaged devices consist of any device that connects to the network, cloud resources, or other assets without corporate-controlled security. How Does Remote Encryption Work?

Security Affairs
JANUARY 5, 2024
Ivanti fixed a critical vulnerability in its Endpoint Manager (EPM) solution that could lead to remote code execution (RCE) on vulnerable servers Ivanti has released security updates to address a critical vulnerability, tracked as CVE-2023-39336 (CVSS score 9.6), impacting its Endpoint Manager (EPM) solution.

The Last Watchdog
AUGUST 8, 2023
LAS VEGAS — Shadow IT and BYOD security exposures have long bedeviled businesses – ever since the iPhone and Dropbox first came on the scene. Covid 19 only intensified the problem of how to securely manage the personally owned devices and unvetted apps employees gravitate to. We’re truly in an arms race,” he says. “As
Security Affairs
OCTOBER 16, 2023
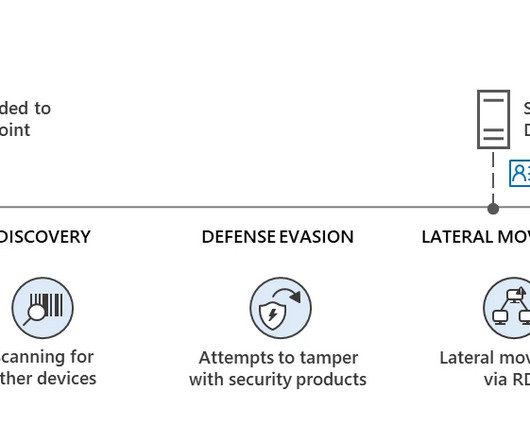
Microsoft announced that its Microsoft Defender for Endpoint helped to block a large-scale hacking campaign carried out by Akira ransomware operators (tracked by Microsoft as Storm-1567) The attack took place in early June 2023 and aimed at an industrial engineering organization. ” reads the analysis published by Microsoft.

Data Breach Today
APRIL 6, 2021
This is reality for most enterprises today, and it’s changed the role of endpoint security solutions. Cisco’s Elias Levy on the Leap From EDR to XDR and What It Means Exponentially more devices on the network mean proportionately less visibility.

Jamf
AUGUST 9, 2023
In this webinar series, Aaron Webb explains what security frameworks are, their importance and explains the critical role they play when securing your organization’s environment.

Thales Cloud Protection & Licensing
MARCH 6, 2024
API Security in 2024: Imperva Report Uncovers Rising Threats and the Urgent Need for Action madhav Thu, 03/07/2024 - 04:56 APIs (Application Programming Interfaces) are the backbone of modern digital innovation. Attackers increasingly exploit vulnerabilities, frequently targeting API business logic to bypass traditional security measures.

OpenText Information Management
MARCH 28, 2024
Environmental Protection Agency and National Security Agency have requested that each U.S. DNS Exfil, SCADA controls, DGA), but also need the additional layer of security that may be missed by using only endpoint protection (e.g. antivirus) or endpoint detection and response (EDR).

Jamf
NOVEMBER 10, 2022
Jamf endpoint security and mobile threat defense solutions offer detection, prevention and remediation capabilities that extend protections across your entire desktop and mobile fleet, protecting devices and empowering users while keeping data secure and maintaining privacy.
Security Affairs
JANUARY 24, 2024
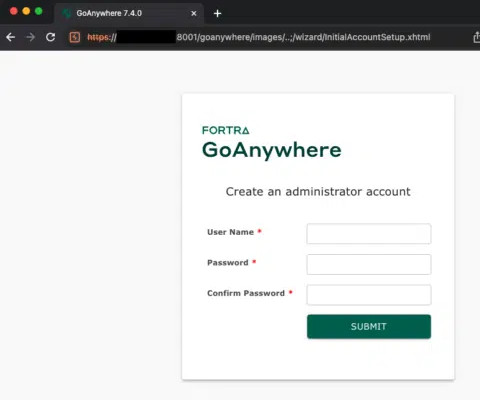
The security experts also published a proof-of-concept (PoC) exploit that allows the creation of new admin users on vulnerable instances exposed online. “The advisory mentions that the endpoint /InitialAccountSetup.xhtml can be deleted and the service restarted to mitigate the issue. . ” continues the analysis.

The Last Watchdog
FEBRUARY 7, 2023
Another report by Vade completed last year found that 87 percent of respondents agreed their organization could take the threat from email security more seriously. Secure email gateways (SEGs) are a common solution used by businesses both large and small to analyze emails for malicious content before they’re able to reach corporate systems.

Jamf
NOVEMBER 13, 2019
Matt Woodruff, Security Solutions Lead, and Andrew Medearis, Senior Product Manager of Jamf Protect, took the stage at JNUC to dive into everything you need to know about Jamf’s latest addition to its product line and why Jamf is expanding into Mac security.

Jamf
NOVEMBER 13, 2019
Matt Woodruff, Security Solutions Lead, and Andrew Medearis, Senior Product Manager of Jamf Protect, took the stage at JNUC to dive into everything you need to know about Jamf’s latest addition to its product line and why Jamf is expanding into Mac security.

Thales Cloud Protection & Licensing
MAY 17, 2023
This results in the malware (binary) to run as a process on the victim’s end user system (endpoint) or server. Exploit Software Vulnerabilities: Cybercriminals can take advantage of security weaknesses in widely used software to gain access to a victim’s system and deploy ransomware.

The Last Watchdog
APRIL 2, 2024
It’s a digital swindle as old as the internet itself, and yet, as the data tells us, the vast majority of security incidents are still rooted in the low-tech art of social engineering. Related: AI makes scam email look real Fresh evidence comes from Mimecast’s “The State of Email and Collaboration Security” 2024 report.

Jamf
JUNE 22, 2022
Endpoint security goes well beyond preventing malware and staying up to date with the latest patches. Endpoint detection and response (EDR), on the other hand, provides a powerful yet intuitive solution.

Jamf
FEBRUARY 15, 2022
Learn how the partnership between Jamf Pro and Google BeyondCorp enables you to construct a compliance and security framework around end-user devices, blending Jamf’s device management with Google’s endpoint management security for a comprehensive, cloud-based, Zero Trust solution.

The Last Watchdog
MARCH 16, 2020
The idea is to divide the network up into segments, called subnetworks, to both optimize performance as well as strengthen security. Related: A use case for endpoint encryption At RSA 2020 in San Francisco recently, I learned about how something called “micro segmentation” is rapidly emerging as a viable security strategy.

Thales Cloud Protection & Licensing
FEBRUARY 21, 2024
Unfortunately, API attacks are increasing as vectors for security incidents. In this blog, we will explain the unique data security challenges for Telcos and three ways how both Thales and Red Hat can help them protect against future API attacks. These volumes are in turn managed by numerous applications and other IT solutions.

Jamf
OCTOBER 6, 2023
Managing and securing your most vulnerable endpoints, mobile devices requires more than just MDM or mobile threat defense solutions. Admins need to be able to converge these technologies as part of their existing security strategy to ensure a strong, organizational security posture.

eSecurity Planet
MARCH 29, 2024
Data loss prevention (DLP) refers to a set of security solutions that identify and monitor information content across storage, operations, and networks. DLP solutions help detect and prevent potential data exposure or leaks. An effective DLP solution provides the security team a complete visibility of their networks.

The Last Watchdog
NOVEMBER 28, 2023
The study, conducted by independent research firm Propeller Insights, dives into how IT business leaders feel about their security posture in a world where the technologies they embrace to grow and thrive are also vulnerable to constant and increasing threats. Human error is among the top causes of security breaches.

The Last Watchdog
MAY 5, 2022
As an enterprise security team, you could restrict internet access at your egress points, but this doesn’t do much when the workforce is remote. Back up your data and secure your backups in an offline location. You’ll significantly reduce your risk if you enforce a minimum security bar for all devices accessing your data.

eSecurity Planet
OCTOBER 8, 2021
And like other old-guard companies, ESET knows it needs to innovate to stay competitive, which the company has done with its cloud-based endpoint protection platform, ESET PROTECT. This article looks at the key features and benefits of the ESET PROTECT Advanced solution. ESET PROTECT Advanced. ESET Competitors.

Security Affairs
JANUARY 17, 2022
Zoho addressed a new critical severity flaw (CVE-2021-44757) that affects its Desktop Central and Desktop Central MSP unified endpoint management (UEM) solutions. Zoho fixed a new critical severity flaw, tracked as CVE-2021-44757, that affects its Desktop Central and Desktop Central MSP unified endpoint management (UEM) solutions.

IBM Big Data Hub
FEBRUARY 16, 2024
Breach and Attack Simulation (BAS) is an automated and continuous software-based approach to offensive security. Similar to other forms of security validation such as red teaming and penetration testing , BAS complements more traditional security tools by simulating cyberattacks to test security controls and provide actionable insights.

Jamf
MARCH 14, 2022
Independent software review sites Capterra and GetApp recognize Jamf Protect, awarding it top marks in the endpoint protection category, recognizing the purpose-built macOS endpoint security solution as a top performer and industry leader for its threat prevention, device health monitoring and unified logging capabilities, among others.
Jamf
NOVEMBER 3, 2022
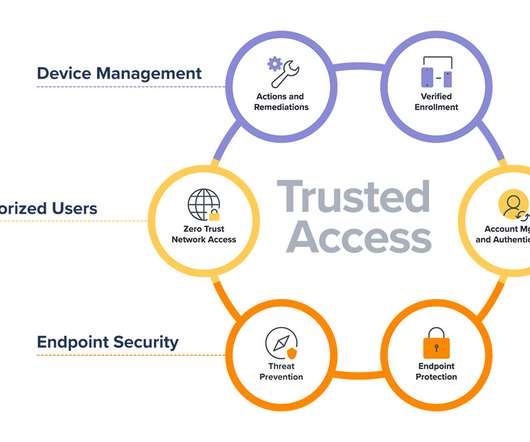
Jamf is uniquely positioned by offering solutions for device management, identity integration workflows and endpoint security. Because these are all from the same vendor, powered by the same platform, and designed to work together, we can achieve an amazing outcome: Trusted Access.

eSecurity Planet
APRIL 5, 2023
To aid in reducing IT labor requirements and to improve security, Extreme Networks created their ExtremeControl network access solution. To compare ExtremeControl against competitors, see our complete list of top network access control (NAC) solutions. Who is Extreme Networks?
Security Affairs
DECEMBER 8, 2023
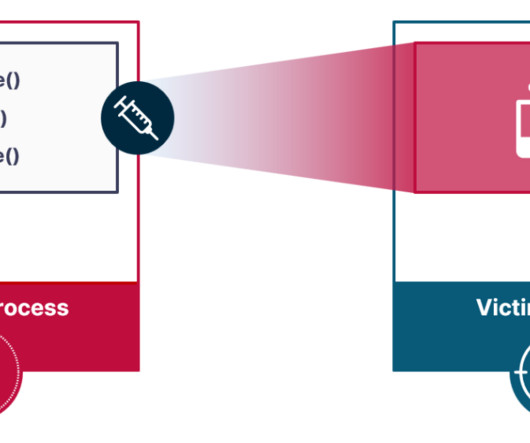
Researchers devised a novel attack vector for process injection, dubbed Pool Party, that evades EDR solutions. Researchers from cybersecurity firm SafeBreach devised a set of process injection techniques, dubbed Pool Party, that allows bypassing EDR solutions. They presented the technique at Black Hat Europe 2023.

Security Affairs
AUGUST 6, 2021
VMware has released security updates to address multiple flaws in its products, including a critical issue that could allow an attacker to access confidential information. reads the security advisory published by the company. reads the security advisory published by the company. ” states the report. Pierluigi Paganini.

IBM Big Data Hub
AUGUST 1, 2023
Trojans, worms and malware are no longer the only cyberthreats keeping IT and security professionals awake at night. According to the IBM Security X-Force Threat Intelligence Index 2023 , for the second year in a row, phishing was the leading cyber threat, identified in 41% of incidents. What is advanced endpoint protection?
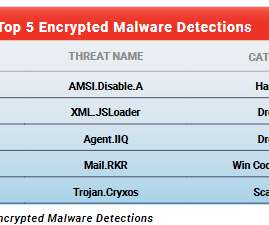
eSecurity Planet
OCTOBER 4, 2021
percent of all malware detected on networks of WatchGuard Technologies customers in the second quarter came over encrypted connections, raising the security risk for the 80 percent of such organizations that lack processes for decrypting and scanning HTTPS traffic for threats. A surprising 91.5 Malware in Encrypted Traffic.

eSecurity Planet
APRIL 14, 2023
As a spinoff of the network infrastructure leader, Juniper Networks, Ivanti’s Policy Secure provides effective network access control built on a foundation of deep understanding of networks. This article will explore the product in depth and explore the features, pros, cons, pricing, and other key aspects of Ivanti’s NAC solution.
Security Affairs
AUGUST 31, 2023
Researchers demonstrated how attackers can abuse the Windows Container Isolation Framework to bypass endpoint security solutions. Researcher Daniel Avinoam at the recent DEF CON hacking conference demonstrated how attackers can abuse the Windows Container Isolation Framework to bypass endpoint security solutions.

Thales Cloud Protection & Licensing
JANUARY 8, 2024
Thales + Imperva: Delivering the Next Generation of Data Security madhav Tue, 01/09/2024 - 05:13 We are pleased to share that Thales has completed its acquisition of Imperva. Imperva is now merging with our Thales Cloud Protection & Licensing Business Line. As we bring our teams together, we are committed to our strategic partners.

Security Affairs
DECEMBER 23, 2021
In a recent wave of attacks, AvosLocker ransomware is rebooting systems into Windows Safe Mode to disable endpoint security solutions. Sophos experts monitoring AvosLocker ransomware attacks, noticed that the malware is rebooting compromised systems into Windows Safe Mode to disable endpoint security solutions.

eSecurity Planet
MAY 25, 2022
An ideal security stack provides continuous protection without gaps. IDS and IPS solutions help fill in the gaps between endpoint protection , firewalls , and other parts of the security stack. In fact, as evidence of their ongoing importance, IDS and IPS features are increasingly becoming part of those other solutions.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content