George Kurtz: There's a Difference Between Price, Total Cost
Data Breach Today
MARCH 5, 2024
Customers are smart enough to recognize the different between the price of a product and the total lifetime cost of operating inferior technology.

 pricing
pricing 
Data Breach Today
MARCH 5, 2024
Customers are smart enough to recognize the different between the price of a product and the total lifetime cost of operating inferior technology.

Data Breach Today
AUGUST 3, 2022
Fortinet Says Price Hikes Have More Than Offset Supply Chain and Geopolitical Issues Fortinet has raised prices on products and services to address macroeconomic challenges including shipping delays, longer activation timelines, and the suspension of sales in Russia.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
JULY 29, 2022
Researchers from IronNet say the prices offered on "Robin Banks" are substantially less than comparable service providers.
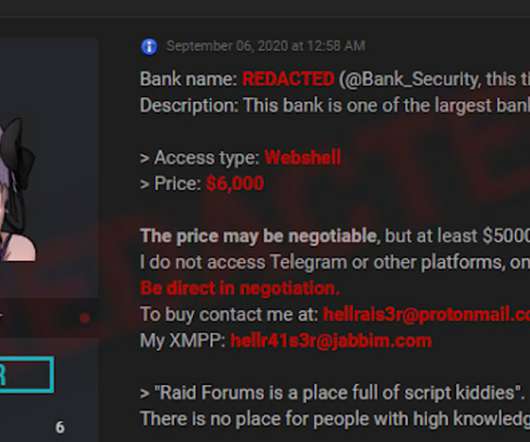
Data Breach Today
APRIL 13, 2021
But researchers say an overabundant supply of access credentials appears to be driving down the prices being commanded on cybercrime forums and markets.

Advertisement
This framework from Software Pricing Partners explains how application enhancements can extend your product offerings.

Data Breach Today
AUGUST 7, 2020
Paper Describes How Connected Devices Could Be Used to Manipulate Markets High-wattage IoT devices and appliances, such as connected refrigerators, air conditioners and heaters, could be turned into massive botnets by malicious actors and used to influence energy prices, according to an academic study released at Black Hat 2020.

Data Breach Today
OCTOBER 31, 2023
Researchers Discover 'Prolific Puma' Service Used by Hackers, Phishers and Scammers Researchers have discovered an underground offering with the codename "Prolific Puma," which since 2020 has been the "largest and most dynamic" cybercrime link-shortening service on the market.

Advertisement
Just by embedding analytics, application owners can charge 24% more for their product. How much value could you add? This framework explains how application enhancements can extend your product offerings. Brought to you by Logi Analytics.

Advertisement
How to price and package predictive analytics with your product. The Definitive Guide to Predictive Analytics has everything you need to get started, including real-world examples, steps to build your models, and solutions to common data challenges. Techniques to solve common data challenges and build performant models.

Advertisement
Inside you will learn: How embedded analytics has become essential to business applications When to buy an embedded analytics solution and when to build one How to go-to-market, from pricing and packaging to external promotion How to build a business case and sell the project internally The future of embedded analytics …plus so much more.

Advertiser: ZoomInfo
Dig into our data-backed guide to learn: Proven methods for warming up cold calls Coaching points for responding to price pressure early and often Front-line examples of how to win the battle for customer retention

Advertiser: ZoomInfo
This buyers guide will cover: Review of important terminology, metrics, and pricing models related to database management projects. Download ZoomInfo’s latest data-driven eBook aimed to help marketing leaders understand the best practices around choosing a B2B contact data provider.

Advertisement
Why do some embedded analytics projects succeed while others fail? We surveyed 500+ application teams embedding analytics to find out which analytics features actually move the needle. Read the 6th annual State of Embedded Analytics Report to discover new best practices. Brought to you by Logi Analytics.

Advertisement
Many application teams leave embedded analytics to languish until something—an unhappy customer, plummeting revenue, a spike in customer churn—demands change. But by then, it may be too late. In this White Paper, Logi Analytics has identified 5 tell-tale signs your project is moving from “nice to have” to “needed yesterday.".

Advertiser: ZoomInfo
You’ll get a deep dive on: Proven methods for warming up cold calls Coaching points for responding to price pressure early and often Front-line examples of how to win the battle for customer retention This guide is designed to help today’s B2B sales leaders ramp up their effectiveness in any economic environment.
Let's personalize your content