Tech CEO Sentenced to 5 Years in IP Address Scheme
Krebs on Security
OCTOBER 17, 2023
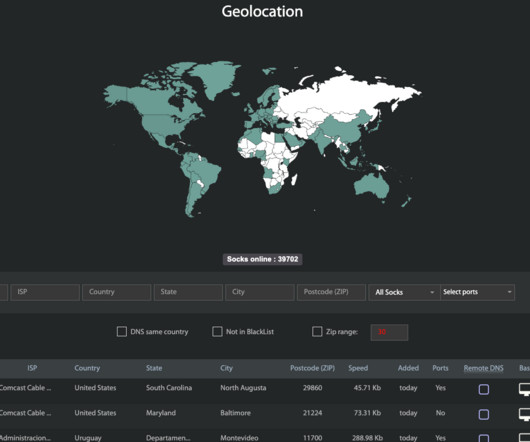
” “Those who seek to defraud ARIN (or other Regional Internet Registries) are subject to costly and serious civil litigation, criminal charges, and, ultimately, a lengthy term of incarceration,” reads a statement from ARIN on Golestan’s sentencing. .” Amir Golestan , the 40-year-old CEO of the Charleston, S.C.















































Let's personalize your content