Database Security Best Practices
eSecurity Planet
MARCH 4, 2021
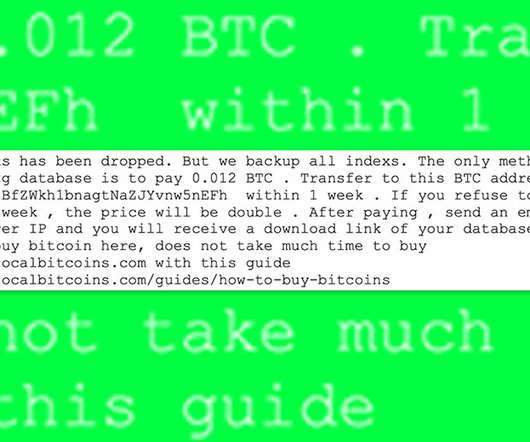
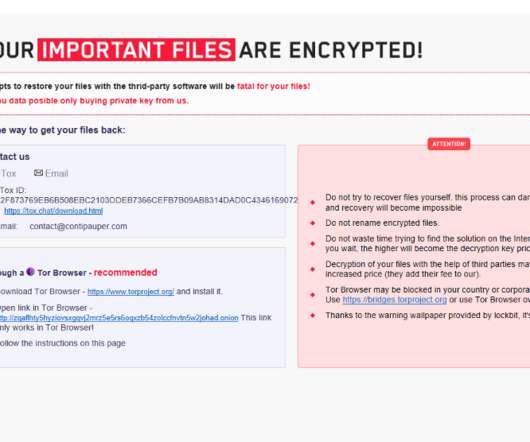
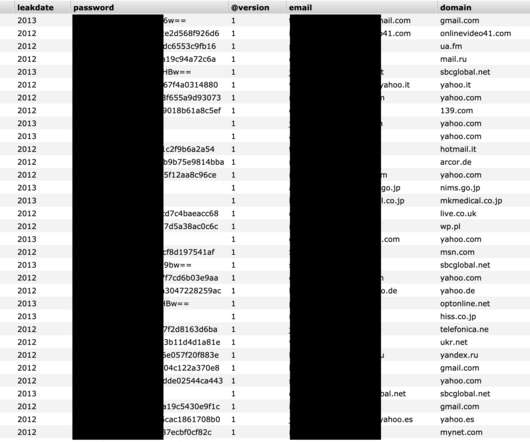
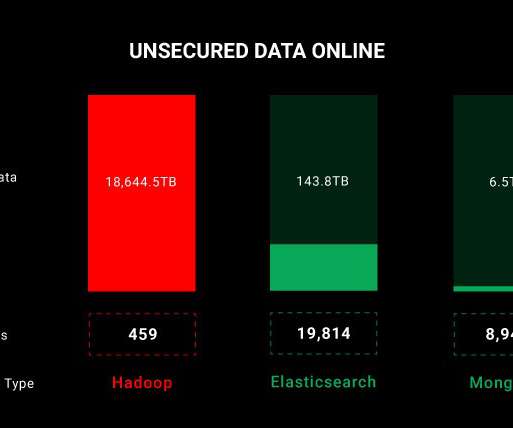
One reality of managing large organizations involves collecting massive amounts of sensitive data that is stored and managed in databases. This makes databases a prime target for cyberattacks. In this article, we cover some database security best practices that can help keep your databases safe from attackers.






































Let's personalize your content