Stop Ransomware in its Tracks With CipherTrust Transparent Encryption Ransomware Protection
Thales Cloud Protection & Licensing
APRIL 16, 2024
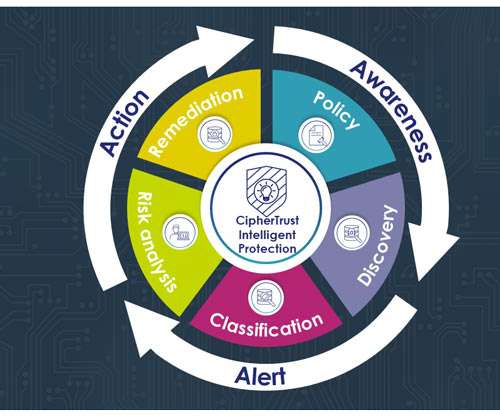
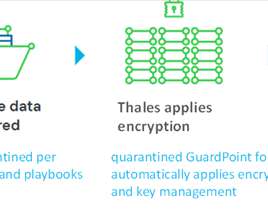
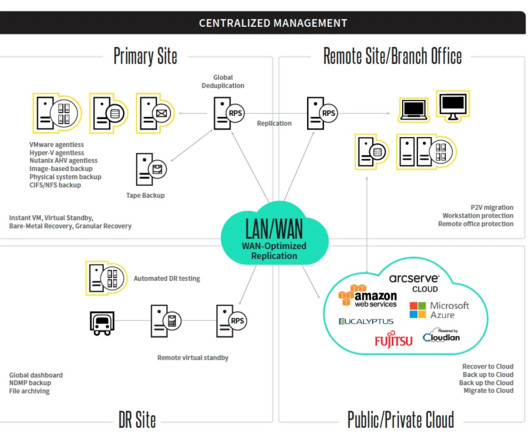
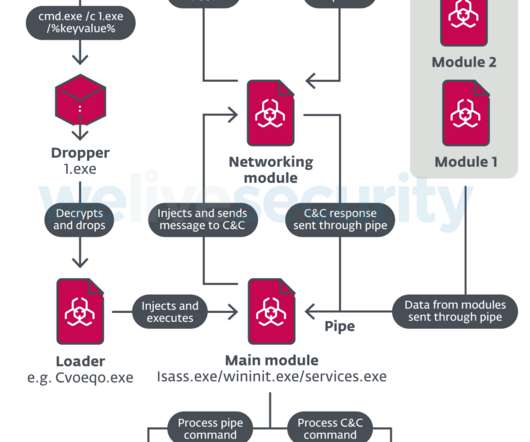
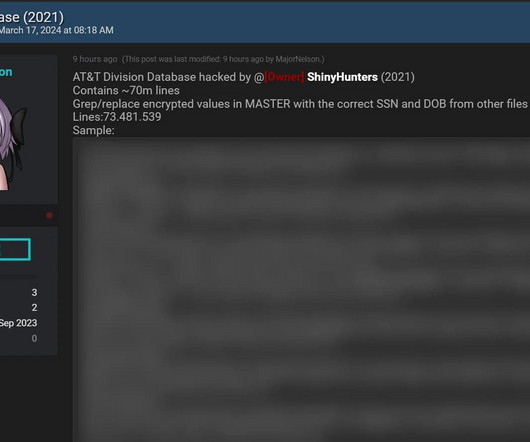
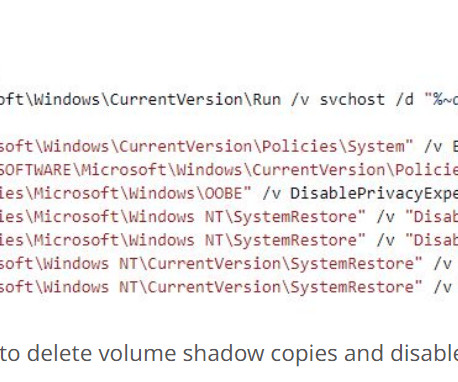
Stop Ransomware in its Tracks With CipherTrust Transparent Encryption Ransomware Protection madhav Wed, 04/17/2024 - 05:22 Our last blog Ransomware Attacks: The Constant and Evolving Cybersecurity Threat described the ever dangerous and evolving cybersecurity threat of ransomware. Behavior-Based Now enter behavior-based solutions.








































Let's personalize your content