Lilith: The Latest Threat in Ransomware
eSecurity Planet
JULY 19, 2022
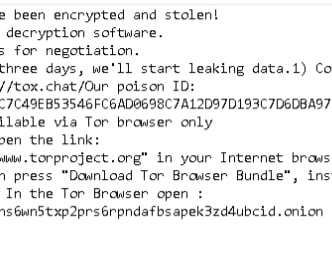
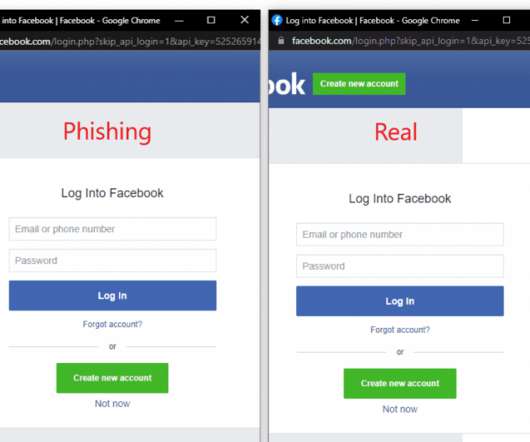
The malware exfiltrates data before encrypting the targeted devices to provide additional means of extortion. The hackers posted their first victim on a data leak site before removing the publication later. lilith” extension to rename encrypted files. How to Protect Against Lilith Ransomware.


















































Let's personalize your content