3 Cybersecurity Myths to Bust
Dark Reading
MAY 11, 2021
Deeply rooted cybersecurity misconceptions are poisoning our ability to understand and defend against attacks.

Dark Reading
MAY 11, 2021
Deeply rooted cybersecurity misconceptions are poisoning our ability to understand and defend against attacks.

Security Affairs
MAY 13, 2021
The recent Colonial Pipeline attack highlights the dangers that are facing Critical Infrastructure worldwide. The attack perpetrated by hackers on oil company Colonial Pipeline highlights the dangers that are facing Industrial Control Systems (ICS) and the need for change in the information security landscape, The attack took place on May 7th where hackers used ransomware to cripple the defense of the company.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
MAY 9, 2021
There's a battle raging over how advertisers can target us on the web—or whether they should be able to target us at all.

Krebs on Security
MAY 14, 2021
The DarkSide ransomware affiliate program responsible for the six-day outage at Colonial Pipeline this week that led to fuel shortages and price spikes across the country is running for the hills. The crime gang announced it was closing up shop after its servers were seized and someone drained the cryptocurrency from an account the group uses to pay affiliates. “Servers were seized (country not named), money of advertisers and founders was transferred to an unknown account,” reads a

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Data Breach Today
MAY 8, 2021
Attackers have Co-Opted Malware For Data Exfiltration and Ransom, Group-IB Finds Attackers have co-opted the Hancitor malware downloader and recently used it to deliver Cuba ransomware as part of an email spam campaign for data exfiltration and ransom extortion, a new report by security firm Group-IB finds.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

AIIM
MAY 11, 2021
A staple of many Information Technology (IT) policy suites is the Acceptable Use Policy (AUP), intended to govern what people working in the organization can and cannot do with the technology we provide them. IIM professionals and consultants push to have these kinds of policies in place, and countless templates and best practices are available on the Internet to use as a starting point if we don't have one already.

Krebs on Security
MAY 11, 2021
Microsoft today released fixes to plug at least 55 security holes in its Windows operating systems and other software. Four of these weaknesses can be exploited by malware and malcontents to seize complete, remote control over vulnerable systems without any help from users. On deck this month are patches to quash a wormable flaw, a creepy wireless bug, and yet another reason to call for the death of Microsoft’s Internet Explorer (IE) web browser.

Data Breach Today
MAY 10, 2021
Report: DarkSide Ransomware Gang Infected Fuel Supplier Colonial Pipeline Company has restored smaller pipelines that ship fuels to the U.S. East Coast after a ransomware incident, but its larger ones are still offline as it assesses safety. Citing U.S. officials, the Associated Press reports the company was infected by the DarkSide ransomware group.

The Last Watchdog
MAY 11, 2021
By patiently slipping past the best cybersecurity systems money can buy and evading detection for 16 months, the perpetrators of the SolarWinds hack reminded us just how much heavy lifting still needs to get done to make digital commerce as secure as it needs to be. Related: DHS launches 60-day cybersecurity sprints. Obviously, one change for the better would be if software developers and security analysts paid much closer attention to the new and updated coding packages being assembled and depl

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Dark Reading
MAY 10, 2021
As the massive US pipeline operator works to restore operations after a DarkSide ransomware attack late last week, experts say it's a cautionary tale for critical infrastructure providers.

Schneier on Security
MAY 10, 2021
This is a newly unclassified NSA history of its reaction to academic cryptography in the 1970s: “ New Comes Out of the Closet: The Debate over Public Cryptography in the Inman Era ,” Cryptographic Quarterly , Spring 1996, author still classified.

Data Breach Today
MAY 10, 2021
Pharmacy Administration Vendor, EMR Hosting Firm Among Latest Victims Two companies that serve the healthcare sector have reported disruptive cyber incidents affecting their clients, the latest in a string of similar supply chain incidents.

The Last Watchdog
MAY 10, 2021
The value of sharing threat intelligence is obvious. It’s much easier to blunt the attack of an enemy you can clearly see coming at you. Related: Supply chains under siege. But what about trusted allies who unwittingly put your company in harm’s way? Third-party exposures can lead to devastating breaches, just ask any Solar Winds first-party customer.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Security Affairs
MAY 10, 2021
The U.S. FBI confirmed that the attack against the Colonial Pipeline over the weekend was launched by the Darkside ransomware gang. The U.S. Federal Bureau of Investigation confirmed that the Colonial Pipeline was shut down due to a cyber attack carried out by the Darkside ransomware gang. “The FBI confirms that the Darkside ransomware is responsible for the compromise of the Colonial Pipeline networks.

Threatpost
MAY 11, 2021
A patch for Adobe Acrobat, the world’s leading PDF reader, fixes a vulnerability under active attack affecting both Windows and macOS systems that could lead to arbitrary code execution.

Data Breach Today
MAY 11, 2021
City Shuts Down Websites, Systems Tulsa city officials shut down systems and websites after a Sunday ransomware attack, making it impossible for residents to gain online access to many services.

The Last Watchdog
MAY 13, 2021
In a day and age when the prime directive for many organizations is to seek digital agility above all else, cool new apps get conceived, assembled and deployed at breakneck speed. Related: DHS instigates 60-day cybersecurity sprints. Software developers are king of the hill; they are the deeply-committed disciples pursuing wide open, highly dynamic creative processes set forth in the gospels of DevOps and CI/CD.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
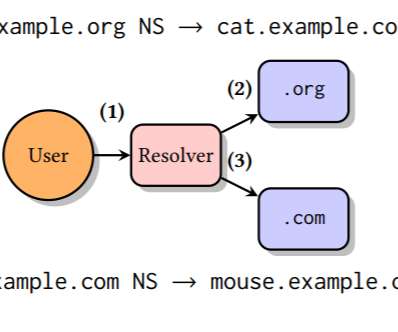
Security Affairs
MAY 9, 2021
A flaw in some DNS resolvers, tracked as TsuNAME, can allow attackers to launch DDoS attacks against authoritative DNS servers. Researchers at SIDN Labs (the R&D team of the registry for.nl domains), InternetNZ (the registry for.nz domains), and the Information Science Institute at the University of Southern California has discovered a vulnerability, named TsuNAME, in some DNS resolvers.

Dark Reading
MAY 11, 2021
Several recent cyber incidents targeting critical infrastructure prove that no open society is immune to attacks by cybercriminals. The recent shutdown of key US energy pipeline marks just the tip of the iceberg.

Data Breach Today
MAY 14, 2021
Colonial Pipeline Attack Used DarkSide Malware The gang behind DarkSide ransomware, which U.S. authorities say was used in the attack against Colonial Pipeline Co., says it's closed its ransomware-as-a-service operation after losing access to part of its infrastructure.

The Last Watchdog
MAY 12, 2021
A new report from Sophos dissects how hackers spent two weeks roaming far-and-wide through the modern network of a large enterprise getting into a prime position to carry out what could’ve been a devasting ransomware attack. Related: DHS embarks on 60-day cybersecurity sprints. This detailed intelligence about a ProxyLogon-enabled attack highlights how criminal intruders are blending automation and human programming skills to great effect.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Security Affairs
MAY 8, 2021
A cyberattack forced the shutdown of one of the largest pipelines in the United States, the Colonial Pipeline facility in Pelham, Alabama. The Colonial Pipeline facility in Pelham, Alabama was hit by a cybersecurity attack, its operators were forced to shut down its systems. The pipeline allows carrying 2.5 million barrels of refined gasoline and jet fuel each day up the East Coast from Texas to New York, it covers 45 percent of the East Coast’s fuel supplies. “The operator of the system,

Schneier on Security
MAY 10, 2021
This is a major story : a probably Russian cybercrime group called DarkSide shut down the Colonial Pipeline in a ransomware attack. The pipeline supplies much of the East Coast. This is the new and improved ransomware attack: the hackers stole nearly 100 gig of data, and are threatening to publish it. The White House has declared a state of emergency and has created a task force to deal with the problem, but it’s unclear what they can do.

Data Breach Today
MAY 14, 2021
The Debate Over Impact of Colonial Pipeline's Apparent Ransom Payment Some cybersecurity experts question the contentions of Speaker of the House Nancy Pelosi and another member of Congress, who say a $5 million ransom reportedly paid by Colonial Pipeline Co. after being hit by DarkSide ransomware would serve as a catalyst for attacks on other critical infrastructure providers.

The Last Watchdog
MAY 14, 2021
It’s accurate to say that security has been bolted onto modern business networks. It also has become very clear that we won’t achieve the full potential of digital transformation without security somehow getting intricately woven into every layer of corporate IT systems. We’re still a long way from achieving that, but a promising roadmap has emerged.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Security Affairs
MAY 10, 2021
The city of Tulsa, Oklahoma, has been hit by a ransomware attack over the weekend that impacted its government’s network and shut down its websites. One of the biggest cities in the US by population size, the City of Tulsa, was victim of a ransomware attack that affected its government’s network and forced the shutdown of official websites over the weekend.

AIIM
MAY 13, 2021
The phrase " the art of the possible " can mean different things to different people. For those of us in the information management business, it has come to mean "achieving what we can (possible), rather than what we want (often impossible)." For me, it's an optimistic view of the future rather than a fearful acknowledgment of our challenges and difficulties.

Data Breach Today
MAY 13, 2021
Order Emphasizes Partnerships, IT Modernization and Supply Chain Security President Joe Biden signed an extensive executive order Wednesday, detailing the government's plan to increase cybersecurity protection across the public and private sectors, as well as securing the nation's infrastructure against the type of attack that targeted SolarWinds and its customers.
Let's personalize your content