Reinventing Professional Services: Tomorrow’s Jobs Today
Information Governance Perspectives
JULY 6, 2021
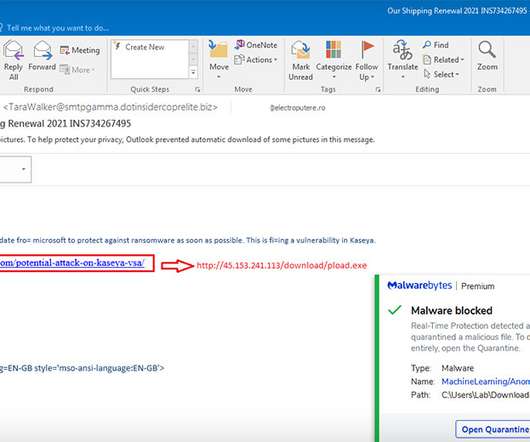
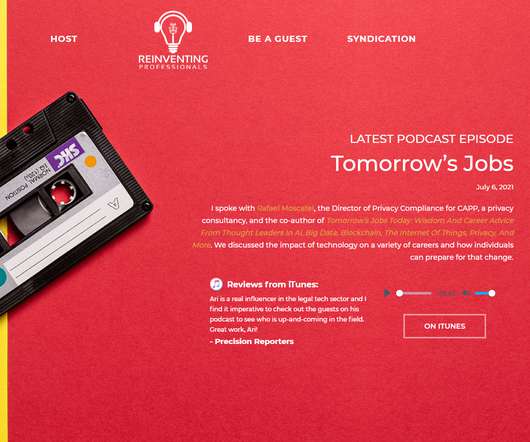
ector of Privacy Compliance for CAPP, a privacy consultancy, and the co-author of Tomorrow’s Jobs Today: Wisdom And Career Advice From Thought Leaders In Ai, Big Data, Blockchain, The Internet Of Things, Privacy, And More. They discussed the impact of technology on a variety of careers and how individuals can prepare for that change. The post Reinventing Professional Services: Tomorrow’s Jobs Today appeared first on Rafael Moscatel.
































Let's personalize your content