GUEST ESSAY: Taking a fresh approach to privileged access management — to curtail abuse
The Last Watchdog
JUNE 21, 2023
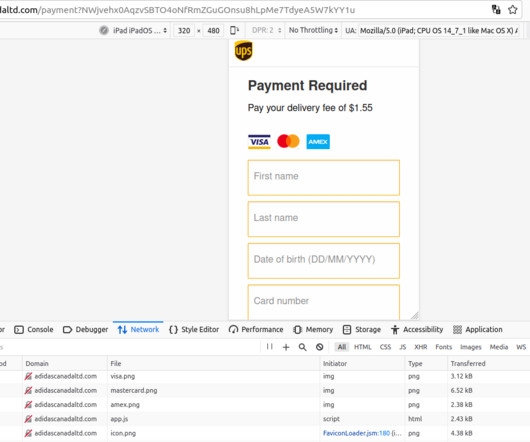
To be productive in an interconnected work environment, employees need immediate access to numerous platforms, both on- and off-premises. Related: Why SMBs need to do PAM well Keeping track of user activity and effecting proper on- and off-boarding are becoming more and more difficult, even as unauthorized access via unused, expired, or otherwise compromised access credentials has become the number one cybersecurity threat vector.






































Let's personalize your content