Reports: Russian IPs Scanning US Energy Firms, Others
Data Breach Today
MARCH 23, 2022
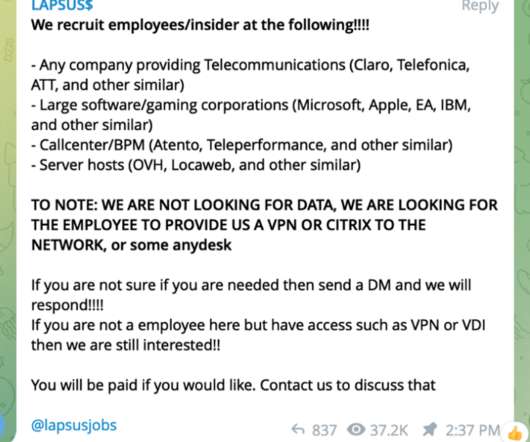
Bulletin Reportedly Issued Just Days Before Biden Warned of Cyber Activity Just days before U.S. President Joe Biden warned that intelligence is pointing toward potential Russian cyberattacks against the U.S., the FBI reportedly issued an urgent bulletin contending that Russian IP addresses have conducted network scanning activity on at least five U.S. energy firms.








































Let's personalize your content