News alert: Incogni study reveals overwhelming majority of spam calls originate locally
The Last Watchdog
JANUARY 17, 2024
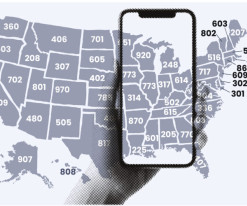
Los Angeles, Calif., Jan. 17, 2024 – Spam calls continue to be a major nuisance in the US, and advice on how to avoid them abound. Incogni’s latest research challenges prevalent assumptions about spam calls, revealing that traditional advice on avoiding specific area codes is largely ineffective. The study, based on the latest data from the Federal Trade Commission (FTC), demonstrates that, contrary to popular belief, a staggering 59.81% of all unwanted calls originate from local num







































Let's personalize your content