Lessons in Threat Detection for Insider Threats
Data Breach Today
DECEMBER 7, 2023
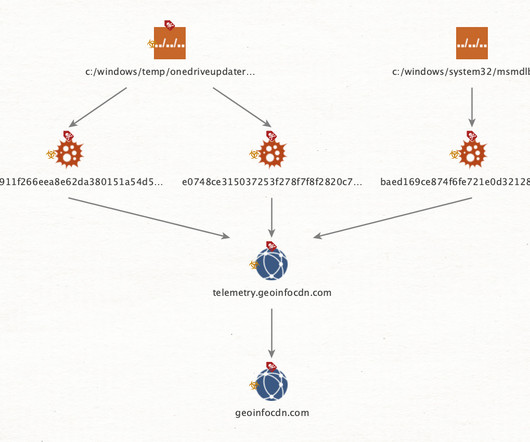
The Risk of Insider Threats Is Growing, But So Are Methods to Detect Them Whether because they're malicious, oblivious to company rules or outsmarted by hackers, insiders pose a mounting degree of risk to companies. Hunting for outside hackers offers lessons in preventing insider incidents, said Thomas Etheridge, CrowdStrike chief global professional services officer.




































Let's personalize your content