Safe, Secure, Anonymous, and Other Misleading Claims
Troy Hunt
OCTOBER 4, 2023
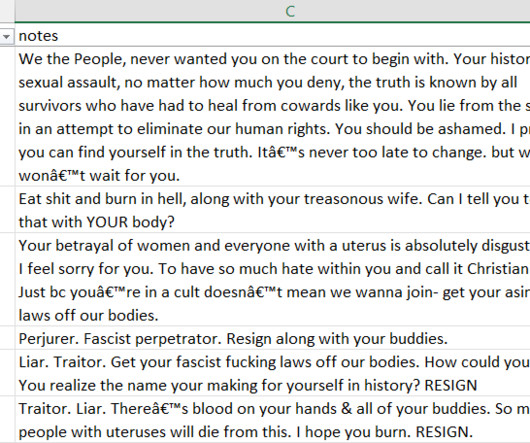
Imagine you wanted to buy some s**t on the internet. Not the metaphorical kind in terms of "I bought some random s**t online", but literal s**t. Turds. Faeces. The kind of thing you never would have thought possible to buy online until. Shitexpress came along. Here's a service that enables you to send an actual piece of smelly s**t to "An irritating colleague.







































Let's personalize your content