3 Classes of Account Fraud That Can Cost Your Company Big Time
Dark Reading
MARCH 22, 2021
Understanding each one can go a long way toward demystifying the topic as a whole - and combatting the threat.

Dark Reading
MARCH 22, 2021
Understanding each one can go a long way toward demystifying the topic as a whole - and combatting the threat.
AIIM
MARCH 23, 2021
Many organizations have an obligation to maintain the information they create and receive as part of regular business activities and to ensure that the information is secured and maintained in official filing systems. But, with an endless amount of information flowing in and out of your business on a daily basis - how do you determine what to capture and what to avoid?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

erwin
MARCH 25, 2021
erwin recently hosted the second in its six-part webinar series on the practice of data governance and how to proactively deal with its complexities. Led by Frank Pörschmann of iDIGMA GmbH, an IT industry veteran and data governance strategist, the second webinar focused on “ The Value of Data Governance & How to Quantify It.”. As Mr. Pörschmann highlighted at the beginning of the series, data governance works best when it is strongly aligned with the drivers, motivations and goals of the bu

Data Breach Today
MARCH 21, 2021
BIG-IP Server Flaw Ranked 9.8 out of 10 in Severity Threats actors are actively exploiting a critical remote code vulnerability in F5 Networks' BIG-IP server appliances, for which patches were released by the company on March 10. The vulnerability has a CVSS ranking of 9.8 out of 10 - highly critical.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.
Krebs on Security
MARCH 23, 2021
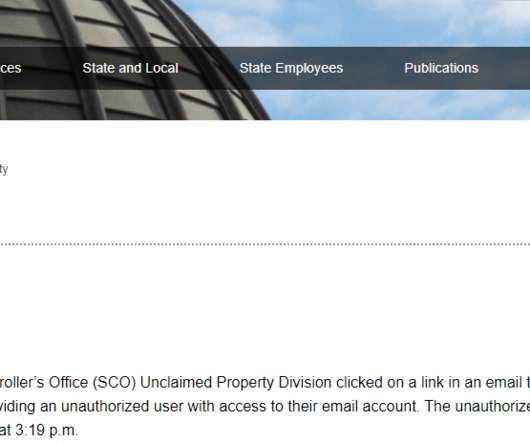
A phishing attack last week gave attackers access to email and files at the California State Controller’s Office (SCO), an agency responsible for handling more than $100 billion in public funds each year. The phishers had access for more than 24 hours, and sources tell KrebsOnSecurity the intruders used that time to steal Social Security numbers and sensitive files on thousands of state workers, and to send targeted phishing messages to at least 9,000 other workers and their contacts.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Security Affairs
MARCH 26, 2021
The Federal Bureau of Investigation (FBI) issued an alert to warn that the Mamba ransomware is abusing the DiskCryptor open source tool to encrypt entire drives. The Federal Bureau of Investigation (FBI) published an alert to warn that the Mamba ransomware is abusing the DiskCryptor open-source tool (aka HDDCryptor, HDD Cryptor) to encrypt entire drives.

Data Breach Today
MARCH 21, 2021
PC and Device Maker Appears to Have Been Targeted by REvil Acer, one of the world's largest PC and device makers, has reportedly been targeted by the ransomware gang REvil, aka Sodinokibi, according to multiple published reports. To date, the Taiwanese company has not confirmed it has been attacked, but data has been posted to the gang's darknet site.

Schneier on Security
MARCH 26, 2021
Lukasz Olejnik has a good essay on hacking weapons systems. Basically, there is no reason to believe that software in weapons systems is any more vulnerability free than any other software. So now the question is whether the software can be accessed over the Internet. Increasingly, it is. This is likely to become a bigger problem in the near future.

IT Governance
MARCH 25, 2021
Cyber Essentials is one of the most cost-effective ways of bolstering your organisation’s information security. The UK government-backed scheme is designed to help organisations address common weaknesses without having to spend a fortune overhauling their cyber security practices. In this blog, we explain the costs involved in Cyber Essentials certification, including consultancy fees, renewal and advancing to Cyber Essentials Plus.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Security Affairs
MARCH 26, 2021
Accenture security researchers published an analysis of the latest Hades campaign, which is ongoing since at least December 2020. . Accenture’s Cyber Investigation & Forensic Response (CIFR) and Cyber Threat Intelligence (ACTI) teams published an analysis of the latest campaign conducted by financially motivated threat group Hades which have been operating since at least December 2020. .
Data Breach Today
MARCH 24, 2021
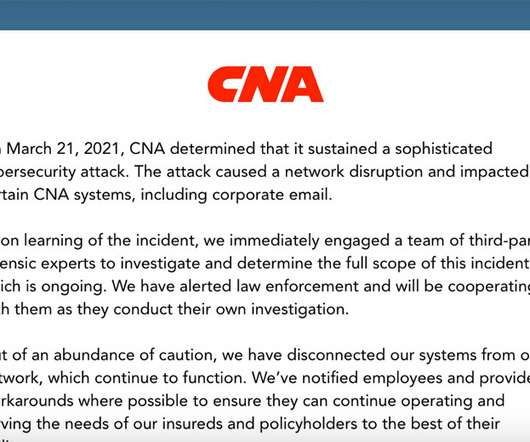
Investigation Continues; Law Enforcement Notified Insurance provider CNA reported Tuesday it was victimized over the weekend by a "cybersecurity attack" that caused a network disruption and impacted certain systems, including corporate email.

Schneier on Security
MARCH 22, 2021
This is a longish video that describes a profitable computer banking scam that’s run out of call centers in places like India. There’s a lot of fluff about glitterbombs and the like, but the details are interesting. The scammers convince the victims to give them remote access to their computers, and then that they’ve mistyped a dollar amount and have received a large refund that they didn’t deserve.

Threatpost
MARCH 24, 2021
Thrive Themes has recently patched vulnerabilities in its WordPress plugins and legacy Themes - but attackers are targeting those who haven't yet applied security updates.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
Security Affairs
MARCH 20, 2021
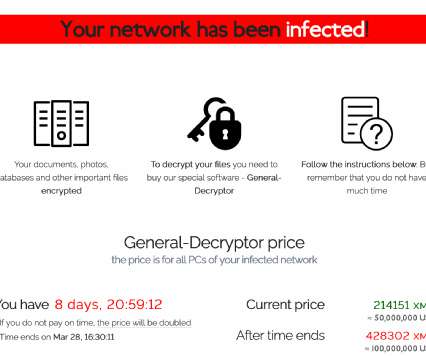
Taiwanese multinational hardware and electronics corporation Acer was victim of a REvil ransomware attack, the gang demanded a $50,000,000 ransom. Taiwanese computer giant Acer was victim of the REvil ransomware attack, the gang is demanding the payment of a $50,000,000 ransom, the largest one to date. Acer is the world’s 6th-largest PC vendor by unit sales as of January 2021, it has more than 7,000 employees (2019) and in 2019 declared 234.29 billion in revenue.

Data Breach Today
MARCH 23, 2021
Brian Byrne and Bastien Latge of EMVCo Discuss Enhancement of Specifications As digital payments have skyrocketed as a result of the surge in e-commerce during the pandemic, more organizations have provided feedback on enhancing EMVCo's specifications to help fight fraud, two executives with the global technical body say.

Schneier on Security
MARCH 24, 2021
It’s not yet very accurate or practical, but under ideal conditions it is possible to figure out the shape of a house key by listening to it being used. Listen to Your Key: Towards Acoustics-based Physical Key Inference. Abstract: Physical locks are one of the most prevalent mechanisms for securing objects such as doors. While many of these locks are vulnerable to lock-picking, they are still widely used as lock-picking requires specific training with tailored instruments, and easily raise

DLA Piper Privacy Matters
MARCH 23, 2021
Authors: Carolyn Bigg and Venus Cheung. Mobile apps have been heavily regulated in China for the last 18 months, under specific TC260 guidelines and CAC circulars. Since these have been in force China mobile app operators have had to comply with a long checklist of specific privacy requirements. Mobile apps have during this period been one of the regulator’s enforcement priorities, and there has been a stream of enforcement action (notably apps taken down from app stores) for non-compliance with

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Security Affairs
MARCH 24, 2021
Security experts reported that a second ransomware gang, named Black Kingdom , is targeting Microsoft Exchange servers. After the public disclosure of ProxyLogon vulnerabilities, multiple threat actors started targeting vulnerable Microsoft Exchange servers exposed online. The first ransomware gang exploiting the above issues in attacks in the wild was a group tracked as DearCry.

Data Breach Today
MARCH 23, 2021
Employee and Customer Information Compromised in January Attack; ICO Investigating British clothing and accessories retailer Fat Face says it detected a data breach in January, which exposed personal information - including partial payment card numbers - for an unspecified number of customers and employees. The Information Commissioner's Office is investigating.

OpenText Information Management
MARCH 25, 2021
Public-sector organizations around the world have made significant progress in improving interactions with their citizen customers by modernizing their infrastructure and digitally transforming the services they deliver. The COVID-19 pandemic highlighted the importance of a consistent, personalized and resilient digital citizen experience. Join me at this year’s OpenText™ World Europe to hear from government agencies … The post Delivering outstanding citizen experience in a post-COVID worl

Threatpost
MARCH 23, 2021
A former IT contractor is facing jailtime after a retaliatory hack into a company’s network and wiping the majority of its employees’ Microsoft Office 365 accounts.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.
Security Affairs
MARCH 20, 2021
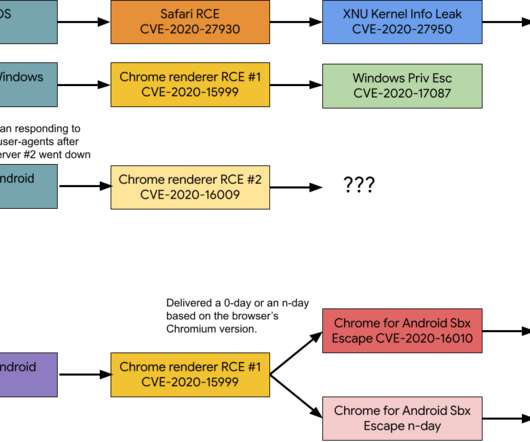
A hacking group has employed at least 11 zero-day flaws as part of an operation that took place in 2020 and targeted Android, iOS, and Windows users. Google’s Project Zero security team published a report about the activity of a mysterious hacking group that operated over the course of 2020 and exploited at least 11 zero-day vulnerabilities in its attacks on Android, iOS, and Windows users.

Data Breach Today
MARCH 23, 2021
Proofpoint Update Describes the Fraud Tactics The SolarWinds supply chain attackers manipulated OAuth app certificates to maintain persistence and access privileged resources, including email, according to researchers at Proofpoint.

DLA Piper Privacy Matters
MARCH 24, 2021
Authors: Carolyn Bigg , Venus Cheung. Operators of e-commerce platforms, websites and apps in China, and those using third party e-commerce, social media or livestreaming platforms to sell their products and services in China, must update their operations, services and systems in advance of wide-ranging new rules. The Measures for the Supervision and Administration of Online Transactions (“Measures”) will come into force on 1 May 2021.

Threatpost
MARCH 23, 2021
Attackers accessed personal and business data from the company’s legacy file-transfer service in a recent data-security incident but core IT systems remained untouched.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
Security Affairs
MARCH 22, 2021
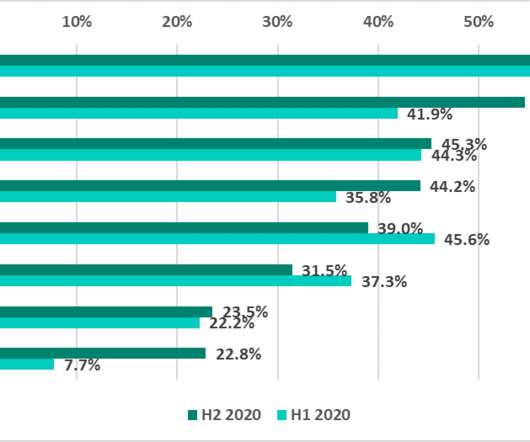
The Kaspersky ICS CERT published a report that provided details about the threat landscape for computers in the ICS engineering and integration sector in 2020. Kaspersky ICS CERT published a report that provided details about the threat landscape for ICS engineering and integration sector in 2020. The experts gathered data related to the cyberthreats that were blocked on computers used to manage industrial control equipment and targeting software used in ICS engineering and integration industry,

Data Breach Today
MARCH 23, 2021
Acting Director Describes Latest Steps in Battle Against Ransomware The Cybersecurity and Infrastructure Security Agency will soon use its new subpoena powers authorized under the 2021 National Defense Authorization Act to help in the battle against ransomware attacks and other cyberthreats, says Brandon Wales, the acting agency director.

Hunton Privacy
MARCH 22, 2021
On March 22, 2021, the Centre for Information Policy Leadership (“CIPL”) at Hunton Andrews Kurth published its paper on delivering a risk-based approach to regulating artificial intelligence (the “Paper”), with the intention of informing current EU discussions on the development of rules to regulate AI. CIPL partnered with key EU experts and leaders in AI in drafting the Paper, translating best practices and emerging policy trends into actionable recommendations for effective AI regulation.
Let's personalize your content