Exploit for Critical Windows Defender Bypass Goes Public
Dark Reading
NOVEMBER 21, 2023
Threat actors were actively exploiting CVE-2023-36025 in Windows SmartScreen as a zero-day vulnerability before Microsoft patched it in November.

Dark Reading
NOVEMBER 21, 2023
Threat actors were actively exploiting CVE-2023-36025 in Windows SmartScreen as a zero-day vulnerability before Microsoft patched it in November.
Data Breach Today
NOVEMBER 23, 2023
Also, Kansas Courts Say Ongoing Outage Traces to Attack; Confidential Data Stolen This week's data breach roundup: Chinese-affiliated hackers target the Philippine government; Kansas Courts confirm data theft; officials warn of exploited flaws in Sophos, Oracle and Microsoft software; AutoZone discloses a Clop ransomware attack; Optus' CEO resigns after network outage.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
NOVEMBER 19, 2023
A hacking gang known as Scattered Spiders soundly defeated the cybersecurity defenses of MGM and Caesars casinos. Related: Russia puts the squeeze on US supply chain This cost the Las Vegas gambling meccas more than $100 million while damaging their reputations. As the companies face nine federal lawsuits for failing to protect customer data, it’s abundantly clear hackers have checkmated multi-factor authentication (MFA).

AIIM
NOVEMBER 21, 2023
Recently, I was lucky enough to be part of a networking group that got to see a real world demo of Chat GPT in a highly practical use case. The use case was focused on internal search within an organization and utilized the strengths of Chat GPT as a Large Language Model (LLM). The organization demonstrating the use case explained they used a conversational use interface (UI) that focused on user experience and making it easier for the user to find the information they were looking for without h

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

WIRED Threat Level
NOVEMBER 20, 2023
A WIRED analysis of leaked police documents verifies that a secretive government program is allowing federal, state, and local law enforcement to access phone records of Americans who are not suspected of a crime.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Security Affairs
NOVEMBER 20, 2023
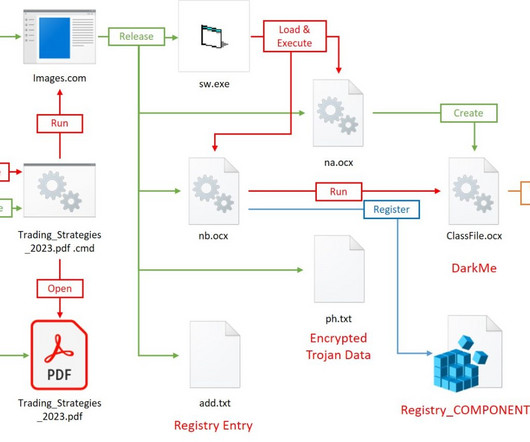
The DarkCasino APT group leveraged a recently disclosed WinRAR zero-day vulnerability tracked as CVE-2023-38831. Researchers at cybersecurity firm NSFOCUS analyzed DarkCasino attack pattern exploiting the WinRAR zero-day vulnerability tracked as CVE-2023-38831. The economically motivated APT group used specially crafted archives in phishing attacks against forum users through online trading forum posts. “DarkCasino is an APT threat actor with strong technical and learning ability, who is g

CGI
NOVEMBER 22, 2023
Founded in 1976, CGI is among the largest IT and business consulting services firms in the world. We are insights-driven and outcomes-based to help accelerate returns on your investments.

WIRED Threat Level
NOVEMBER 21, 2023
The North Atlantic Fellas Organization is trying to shut down Trump’s flailing social media platform before the 2024 election—by shitposting.

Data Breach Today
NOVEMBER 20, 2023
OpenAI Board Thwarts Altman's Return, Names Ex-Twitch Boss Emmett Shear Interim CEO OpenAI co-founders Sam Altman and Greg Brockman will lead a new advanced AI research team at Microsoft after OpenAI's board decided not to bring them back, Satya Nadella said. The nonprofit behind ChatGPT opted instead to name longtime Twitch CEO Emmett Shear as its new interim leader Sunday night.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Security Affairs
NOVEMBER 19, 2023
8Base ransomware operators were observed using a variant of the Phobos ransomware in a recent wave of attacks. Cisco Talos researchers observed 8Base ransomware operators using a variant of the Phobos ransomware in recent attacks. Phobos variants are usually distributed by the SmokeLoader , but in 8Base campaigns, it has the ransomware component embedded in its encrypted payloads.

KnowBe4
NOVEMBER 22, 2023
Another day, another warning about holiday scams! Lookout Inc., a data-centric cloud security company, is warning employees and businesses that phishing attacks are expected to more than double this week , based on historical data. With more corporate data residing in the cloud and a massive amount of employees still working remotely, mobile has become the endpoint of choice for the modern workforce.

WIRED Threat Level
NOVEMBER 23, 2023
There’s a devastating amount of heavy news these days. Psychology experts say you need to know your limits—and when to put down the phone.

Data Breach Today
NOVEMBER 21, 2023
LockBit and Nation-State Groups Using Session Tokens to Access Patched Devices With experts warning that NetScaler ADC and Gateway devices are being exploited by nation-state and cybercrime groups, the manufacturer has again urged all users to "patch immediately as well as terminate active sessions, which attackers can otherwise use to access devices even post-patch.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
Security Affairs
NOVEMBER 23, 2023
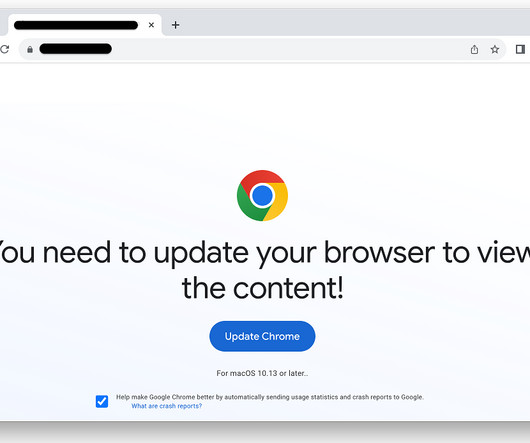
Threat actors spread Atomic Stealer (AMOS) macOS information stealer via a bogus web browser update as part of the ClearFake campaign. Atomic Stealer (AMOS) macOS information stealer is now being delivered via a fake browser update chain tracked as ClearFake, Malwarebytes researchers warn. The malware focuses on macOS, designed to pilfer sensitive information from the compromised systems.

Dark Reading
NOVEMBER 20, 2023
China pairs cyber and kinetic attacks in the South Pacific as it continues to wrangle control of the South China Sea.

KnowBe4
NOVEMBER 21, 2023
Scammers are using a compromised X (formerly Twitter) account belonging to Bloomberg Crypto to send users to a phishing site designed to steal Discord credentials, BleepingComputer reports.

Data Breach Today
NOVEMBER 23, 2023
Also: Kronos Loses $25 Million via API Breach; Regulators Charge Kraken This week's cryptocurrency hack roundup features hackers stealing $87 million from Heco, Kronos reporting $25 million stolen via an API breach, regulators filing charges against Kraken, feds charging three people with stealing $10 million as well as seizing $9 million tied to a pig butchering scam.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
Security Affairs
NOVEMBER 24, 2023
Almost a million files with minors’ data, including home addresses and photos were left open to anyone on the internet, posing a threat to children. During a recent investigation, the Cybernews research team discovered that IT company Appscook – which develops applications used by more than 600 schools in India and Sri Lanka for education management – leaked a staggering amount of sensitive data, including photos of minors, home addresses, and birth certificates, due to a misconfiguration

Dark Reading
NOVEMBER 22, 2023
The actor behind the high-profile MGM incident jumps across segmentations in under an hour, in a ransomware attack spanning Okta, Citrix, Azure, SharePoint, and more.

IBM Big Data Hub
NOVEMBER 20, 2023
Advanced organizations know their greatest assets are their employees. However, keeping employees happy and engaged can be challenging, especially when considering available resources and the need to meet other organizational goals. An organization is only as strong as its talent pool, so organizations have increasingly embraced talent management as a core component of their overarching strategy.

Data Breach Today
NOVEMBER 21, 2023
Hacktivists Leak Sensitive Employee Information From Idaho National Laboratory The hacktivist group SiegedSec has taken responsibility for a massive data breach targeting Idaho National Laboratory, a leading nuclear energy testing lab. Concerns are now growing over what data was stolen from the laboratory - and who might have access to it.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Security Affairs
NOVEMBER 24, 2023
Researchers warn of publicly exposed Kubernetes configuration secrets that could pose a threat of supply chain attack for organizations. Aqua Nautilus researchers warn of publicly exposed Kubernetes configuration secrets that put organizations at risk of supply chain attacks. The experts noticed that these misconfigurations impact hundreds of organizations and open-source projects.

KnowBe4
NOVEMBER 21, 2023
I recently wrote about how 1 in 34 organizations globally has experienced an attempted ransomware attack. But that statistic doesn’t provide enough context around the impact felt by the organizations that do business in one form or another with those that are attacked.

IBM Big Data Hub
NOVEMBER 21, 2023
Apache Kafka is a well-known open-source event store and stream processing platform and has grown to become the de facto standard for data streaming. In this article, developer Michael Burgess provides an insight into the concept of schemas and schema management as a way to add value to your event-driven applications on the fully managed Kafka service, IBM Event Streams on IBM Cloud ® What is a schema?

Data Breach Today
NOVEMBER 24, 2023
Parliamentarians Pass Resolution Calling For Immediate Executive Branch Action European lawmakers slammed the EU executive branch's inaction after a parliamentary committee called for tougher rules designed to prevent spyware abuse across the trading bloc. More than half of European Parliament lawmakers backed a resolution demanding rapid action.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
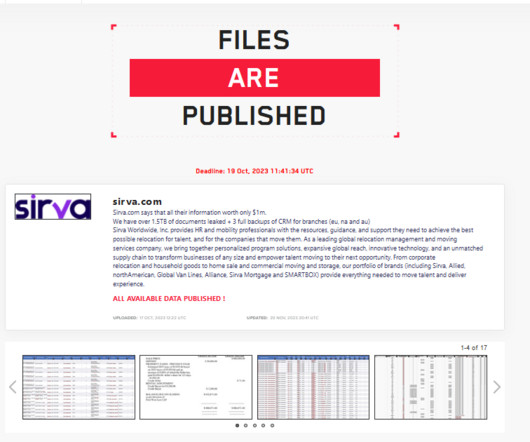
Security Affairs
NOVEMBER 20, 2023
The Canadian government discloses a data breach after threat actors hacked two of its contractors. The Canadian government declared that two of its contractors,Brookfield Global Relocation Services (BGRS) and SIRVA Worldwide Relocation & Moving Services, have been hacked, resulting in the exposure of sensitive information belonging to an undisclosed number of government employees.

KnowBe4
NOVEMBER 22, 2023
Visa Payment Fraud Disruption (PFD) expects phishing attacks to increase between November 2023 and January 2024. Findings in its Holiday Edition Threats Report outline the popular fraud tactics predicted this holiday season.

The Guardian Data Protection
NOVEMBER 21, 2023
Awarding of contract to create new data platform prompts immediate concerns about security of medical records UK politics live – latest updates The NHS has caused controversy by handing the US spy technology company Palantir a £330m contract to create a new data platform, triggering fears about the privacy of patients’ medical details. The move immediately prompted concerns about the security and privacy of patient medical records and the suitability of Palantir to be given access to and oversig
Let's personalize your content