Ransomware Groups Exploiting Unpatched NetScaler Devices
Data Breach Today
OCTOBER 30, 2023
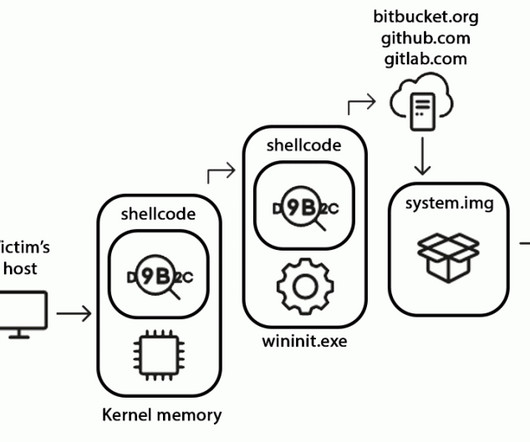
Patch or Perish: Researchers See Mass Exploits of NetScaler ADC and Gateway Devices Ransomware-wielding groups are among the attackers exploiting vulnerabilities in NetScaler devices to bypass authentication and gain initial access to victims' networks. Experts say users must not just patch but also wipe device memory to prevent attackers from bypassing access controls.








































Let's personalize your content