CISA Launches Logging Tool For Resource-Poor Organizations
Data Breach Today
OCTOBER 27, 2023
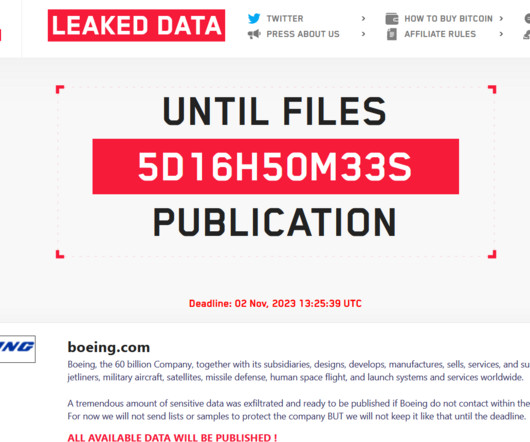
'Logging Made Easy' Provides Organizations With Critical Cybersecurity Insights The U.S. Cybersecurity and Infrastructure Security Agency launched a security tool intended to help organizations with limited resources better protect their Windows-based devices and sensitive data. Logging Made Easy is meant to serve as a turnkey log management tool.









































Let's personalize your content