Python URL parsing function flaw can enable command execution
Security Affairs
AUGUST 12, 2023
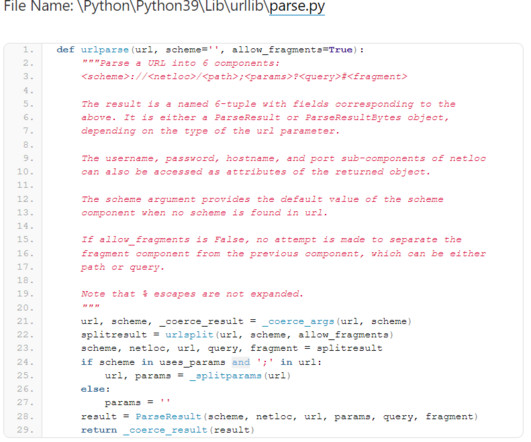
A severe vulnerability in the Python URL parsing function can be exploited to gain arbitrary file reads and command execution. Researchers warn of a high-severity security vulnerability, tracked as CVE-2023-24329 (CVSS score of 7.5), has been disclosed in the Python URL parsing function that could be exploited to bypass blocklisting methods. Successful exploitation of the vulnerability can lead to arbitrary file reads and command execution. “An issue in the urllib.parse component of Pytho















Let's personalize your content