‘The Manipulaters’ Improve Phishing, Still Fail at Opsec
Krebs on Security
APRIL 3, 2024
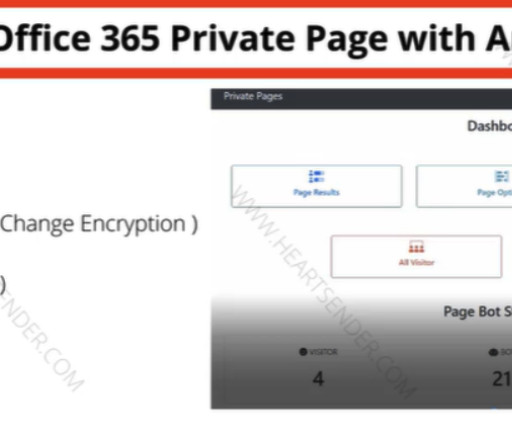
Roughly nine years ago, KrebsOnSecurity profiled a Pakistan-based cybercrime group called “ The Manipulaters ,” a sprawling web hosting network of phishing and spam delivery platforms. In January 2024, The Manipulaters pleaded with this author to unpublish previous stories about their work, claiming the group had turned over a new leaf and gone legitimate.





























Let's personalize your content