Study Downplays Cyber Insurance As Incentive to Pay Ransom
Data Breach Today
JULY 31, 2023
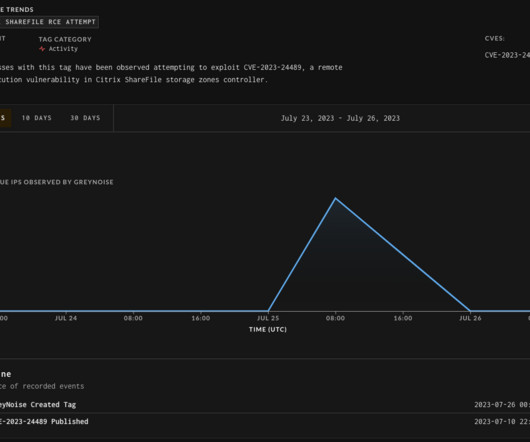
RUSI Study Finds 'No Smoking Gun' Suggesting Insureds Pay Extortion More Readily Fears that cyber insurance coverage drives companies into paying ransomware demands more easily than not appear unfounded, concludes a British think tank study that also suggests insurers should do more to enact corporate discipline. Cyber insurance has been dogged by accusations of moral hazard.





































Let's personalize your content