Comcast Ties Breach Affecting 36M Customers to Citrix Bleed
Data Breach Today
DECEMBER 20, 2023
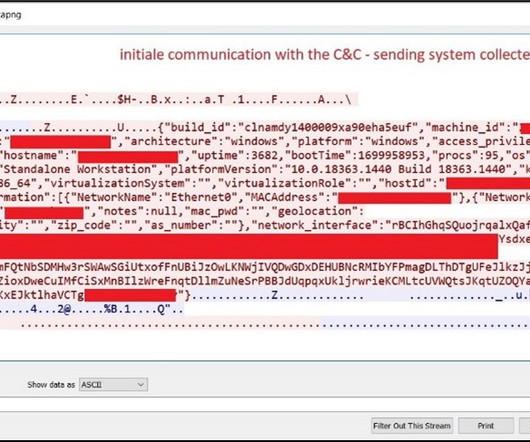
Attackers Apparently Stole Authenticated Sessions to Hit Telecommunications Giant Comcast says attackers stole personal information pertaining to 35.9 million customers of its Xfinity-branded TV, internet and home telephone services in an October attack that targeted a vulnerability - dubbed Citrix Bleed - present in NetScaler and Citrix networking equipment.






































Let's personalize your content