Ransomware Hit Disrupts Real Estate Property Listings in US
Data Breach Today
AUGUST 15, 2023
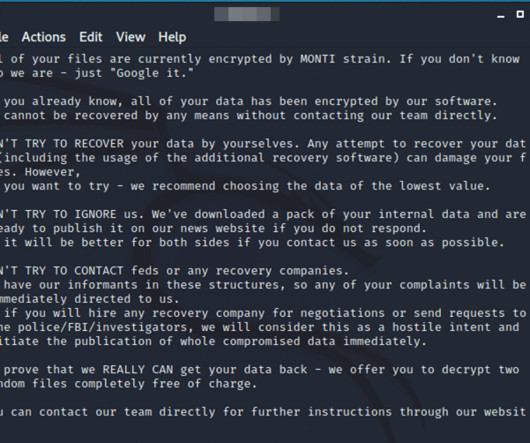
Rapattoni-Hosted Multiple Listing Services Can't Add or Update Property Information Property listings nationwide are being disrupted due to an apparent ransomware attack against California-based Rapattoni, which hosts Multiple Listing Services used by real estate brokers to list, market and sell properties. Rapattoni said it's not clear when its systems might be back online.








































Let's personalize your content