Feds Warn Health Sector of TimisoaraHackerTeam Threats
Data Breach Today
JUNE 19, 2023
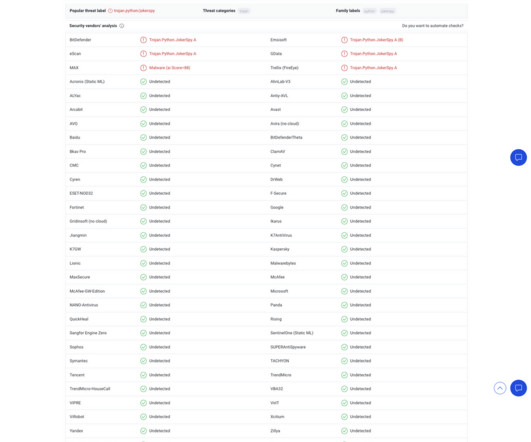
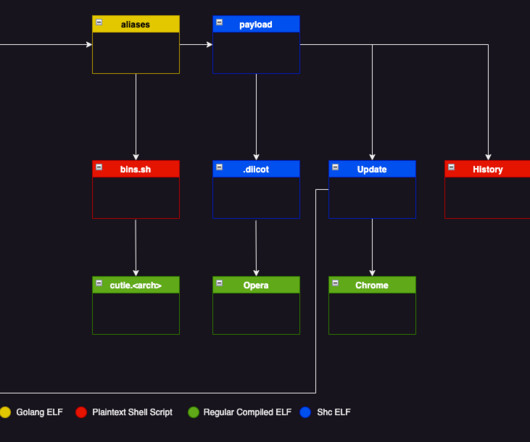
HHS Says 'Obscure' Group Has Resurfaced, Hitting a Cancer Center Federal authorities are warning healthcare and public health sector entities of an apparent resurgence of TimisoaraHackerTeam after an attack in recent weeks by the obscure ransomware group on a U.S. cancer center. HHS says the group was discovered by security researchers in 2018.

































Let's personalize your content