Merry 'Leaksmas'! Hackers Give Away 50 Million Pieces of PII
Data Breach Today
JANUARY 2, 2024
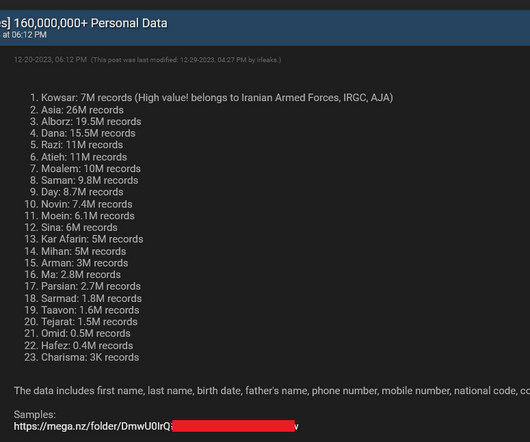
Holiday Leaks Could Result in More Digital Identity Theft and Fraud, Report Warns Hackers celebrated the year-end holidays with a malicious "Free Leaksmas" posting on the dark web, releasing 50 million stolen consumer records, including credit card information. Researchers said the leaked data can be used for identity theft and fraud.
































Let's personalize your content