Known Ransomware Attack Volume Breaks Monthly Record, Again
Data Breach Today
OCTOBER 26, 2023
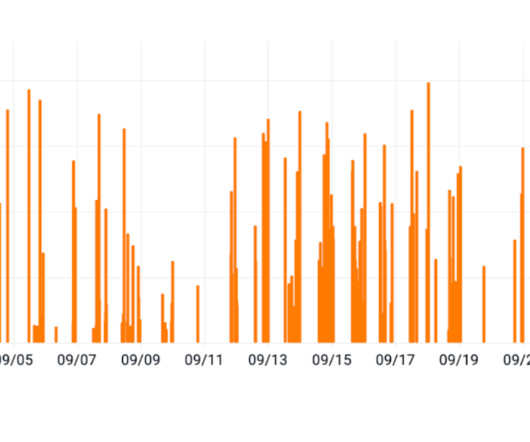
Ransomware Groups Listed 514 Victims in Total on Their Data Leak Sites Last Month The volume of known ransomware attacks surged last month to record-breaking levels, with groups collectively listing 514 victims on their data-leak sites, security researchers report. In the lead: long-timer LockBit followed by newcomer LostTrust, with other new groups also having a notable impact.








































Let's personalize your content