Chinese Hackers Target Routers in IP Theft Campaign
Data Breach Today
SEPTEMBER 27, 2023
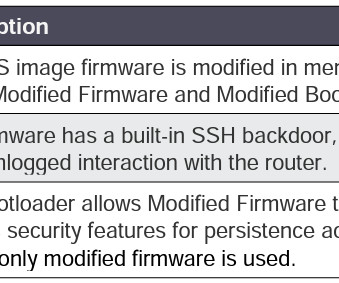
BlackTech Exploits Trusted Relationship Between Outpost and Parent Firm A Chinese hacking group linked to state authorities has upgraded its capabilities to target companies with headquarters in the United States and East Asia, warns an alert from Japanese and American cyber agencies. The group, BlackTech, has a customized firmware backdoor tailored for Cisco routers.








































Let's personalize your content