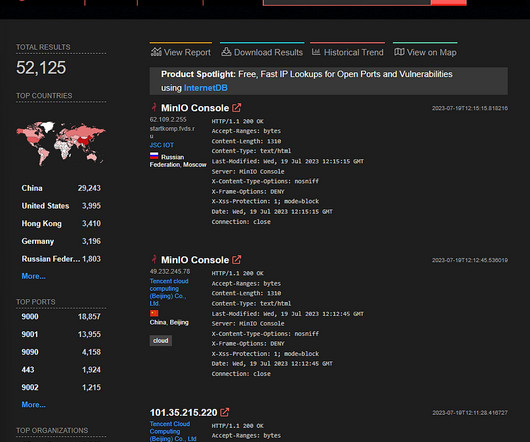
Cybercrime Tremors: Experts Forecast Qakbot Resurgence
Data Breach Today
SEPTEMBER 4, 2023
TrickBot and Emotet Botnets Both Returned After Disruption by Law Enforcement Has the cry of the Qakbot come to an end? While the pernicious, multifunction malware fell quiet last week thanks to Operation "Duck Hunt," lucrative cybercrime operations have a history of rebooting themselves. Rivals also offer ready alternatives to ransomware groups and other criminal users.

























Let's personalize your content