Latest MOVEit Bug Is Another Critical SQL Injection Flaw
Data Breach Today
JULY 7, 2023
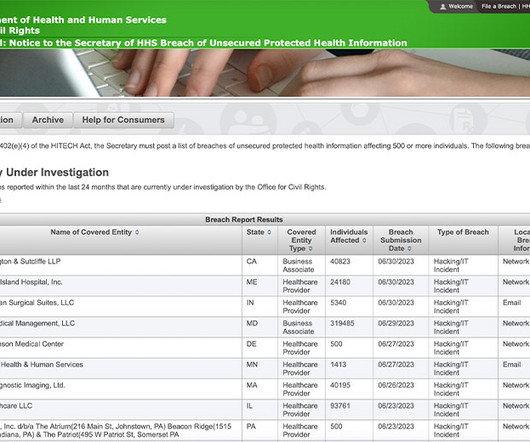
Progress Software Reveals 1 New 'Critical' and 2 'High-Severity' Bugs For the third time since the discovery of the MOVEit Transfer application zero-day vulnerability, Progress Software has revealed a new critical SQL injection vulnerability that allows remote attackers to bypass authentication and execute arbitrary code.








































Let's personalize your content