Apple Fixes Bugs That Infected Egyptian Politician's iPhone
Data Breach Today
SEPTEMBER 22, 2023
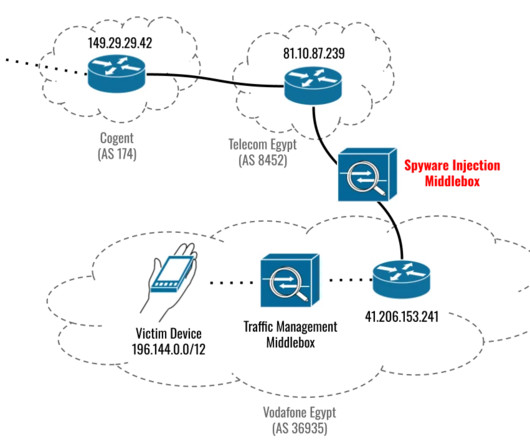
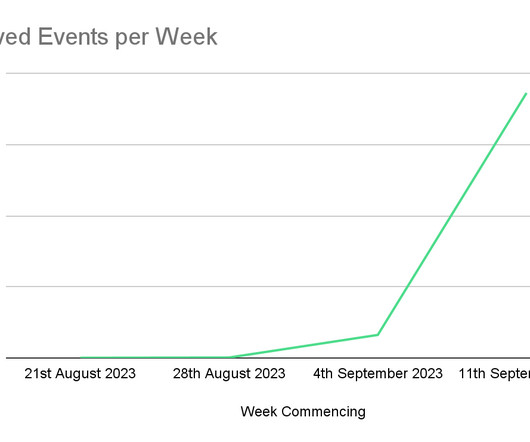
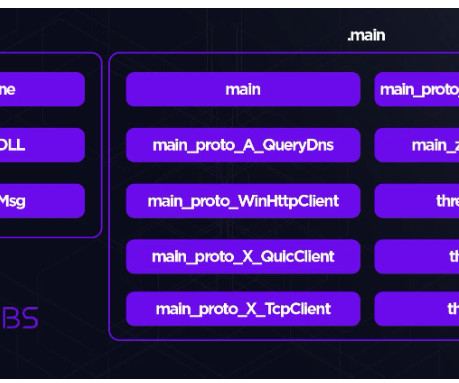
Cytrox's Predator Found on Device of Ahmed Eltantawy Apple released patches Thursday to close three actively exploited vulnerabilities that researchers say commercial spyware maker Cytrox used to infect the iPhone of Egyptian politician Ahmed Eltantawy with Predator malware. The Citizen Lab attributes the attacks to the Egyptian government.







































Let's personalize your content