Ransomware Attack Specialist Tied to Citrix NetScaler Hacks
Data Breach Today
AUGUST 29, 2023
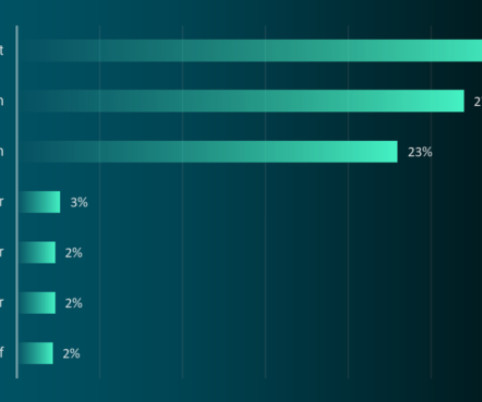
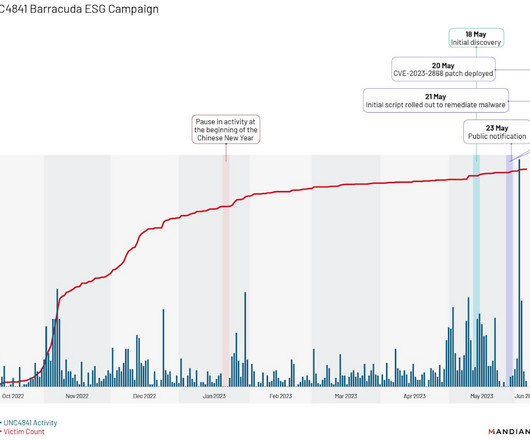
Multiple Highly Automated Campaigns Have Dropped Persistent Web Shells, Experts Say Citrix NetScaler defenders are being warned to not just patch a critical flaw but also review logs from before mid-July for signs of compromise, since attackers - including "a known threat actor specializing in ransomware attacks" - have been dropping web shells that survive patching and rebooting.









































Let's personalize your content