Fidelity National Financial Details LoanCare Breach
Data Breach Today
JANUARY 10, 2024
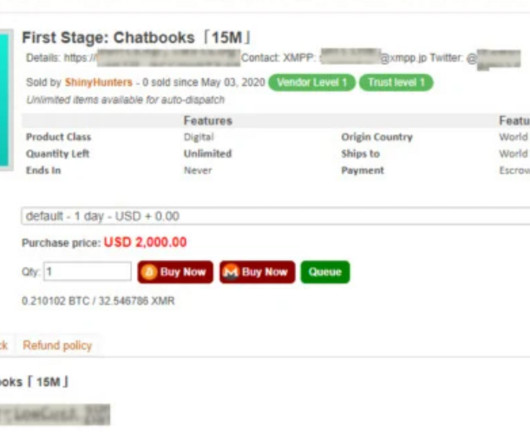
1.3 Million Customers Notified of Breach; BlackCat Ransomware Group Claimed Credit Financial services giant Fidelity National Financial has confirmed that a November 2023 hack attack compromised personal information pertaining to 1.3 million customers of its LoanCare subsidiary. FNF took multiple systems offline when responding to the attack, disrupting some homebuyers.








































Let's personalize your content