Okta Support Unit Breached Via Credential Stolen by Hackers
Data Breach Today
OCTOBER 20, 2023
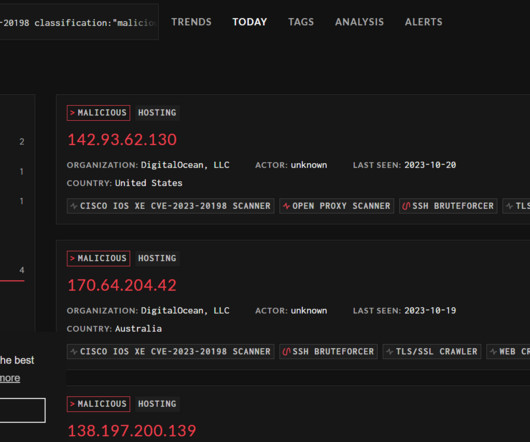
BeyondTrust Says It Took Okta Nearly 3 Weeks to Confirm Breach It First Spotted A breach of Okta's support case management system using a stolen credential allowed attackers to access sensitive files uploaded by the identity security giant's customers. San Francisco-based Okta said the threat actor could view filed uploaded by certain customers as part of recent support cases.









































Let's personalize your content