Medical Transcription Hack Affects 1.2 Million Chicagoans
Data Breach Today
NOVEMBER 8, 2023
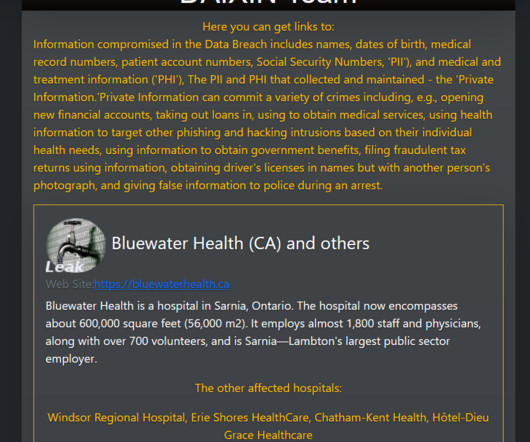
Cook County Health Says It Is Among the Vendor's 'Many' Clients Affected by Hack A major healthcare provider in Chicago that targets underserved populations is notifying 1.2 million patients that their information was compromised in a data theft incident at a medical transcription vendor. The county said it is among "many" entities affected.








































Let's personalize your content