BlackCat Ransomware 'Unseizing' a Dark Web Stunt
Data Breach Today
DECEMBER 19, 2023
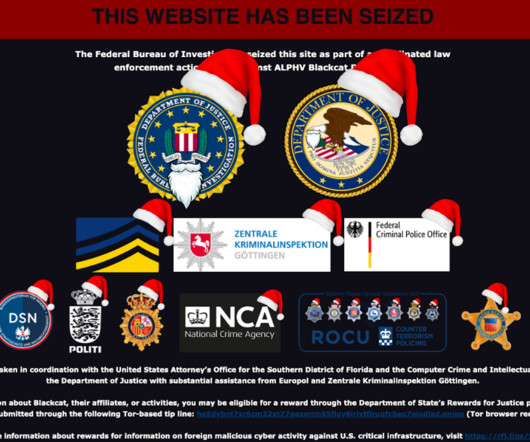
Ransomware Group Declares Nothing Off Limits Outside of CIS Countries The BlackCat ransomware as service operation's putative "unseizing" of its leak site from the FBI is a stunt made possible by way the dark web handles address resolution, security researchers said Monday. The stung was a "tactical error" that could alienate affiliates.







































Let's personalize your content